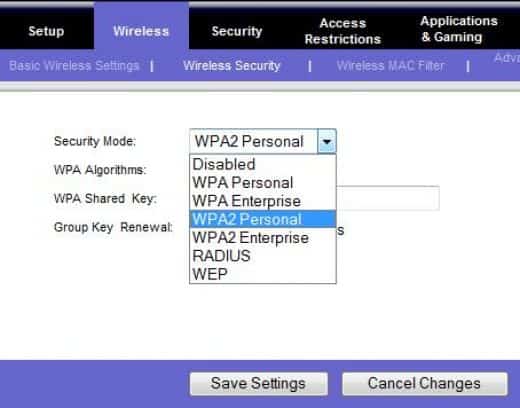
Types of Wi-Fi Encryption You Can Use
There are many types of Wi-Fi encryption you can use on modern Internet routers. So which one should you use? Many people don’t even use encryption, and those that do just pick […]
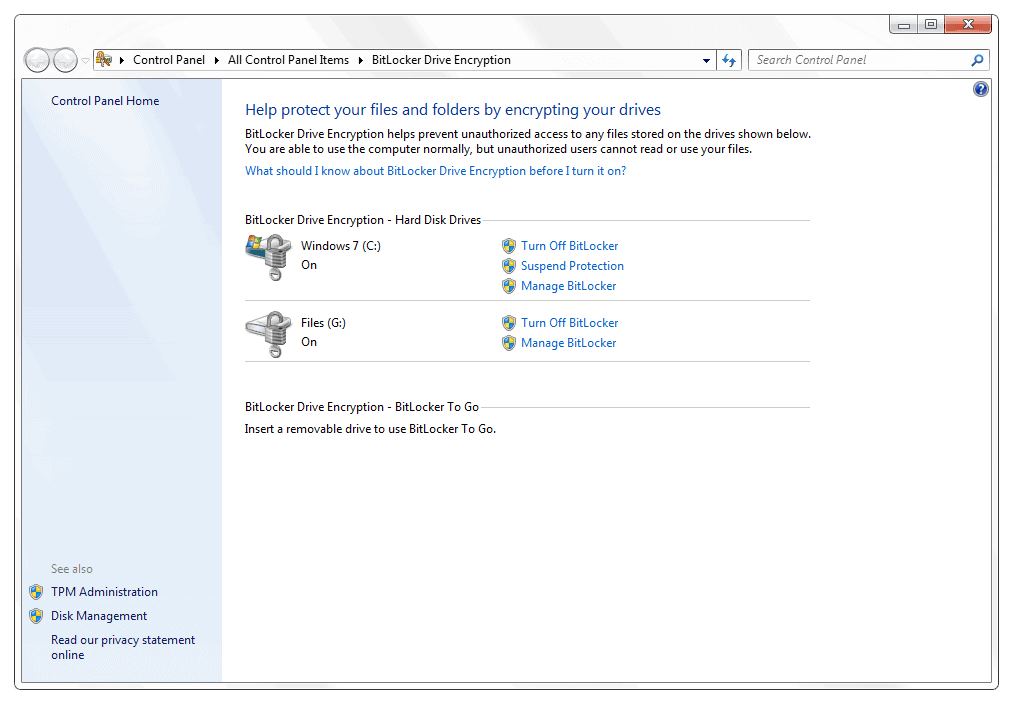
Bitlocker, a Guide for the Uninitiated
BitLocker, first introduced with Windows Vista, is a full drive encryption technology that works with hardware in compatible computers known as a Trusted Platform Module (TPM chip). It offers enterprise-level data encryption […]
MultiObfuscator, Advanced Cryptography Software
Sometimes you may want to protect some files or maybe even just one document from third party access. While you could use an encryption software like TrueCrypt to create a container to […]
TrueCrypt 7.1 Encryption Software Released
I have been using the encryption software TrueCrypt for a long, long time. Cannot really remember when I first started using it but it must have been around the time when Windows […]
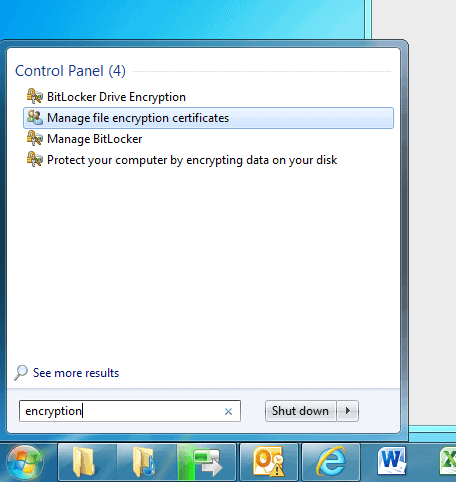
Avoiding EFS Encryption Disasters in Windows
Our data is becoming more and more important to us as we're keeping ever more of our lives on our PCs, tablets, smartphones and in the cloud. Currently there are precious few […]
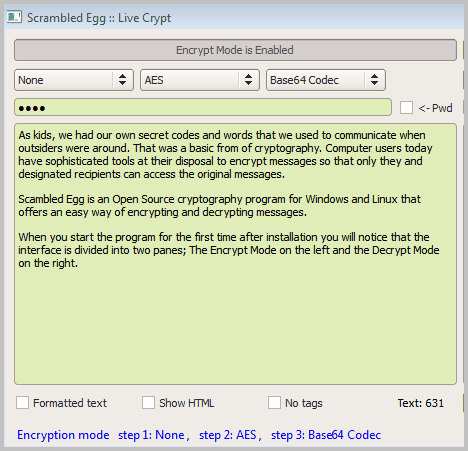
Text Encryption Made Easy With Scrambled Egg
As kids, we had our own secret codes and words that we used to communicate when outsiders were around. That was a basic from of cryptography. Computer users today have sophisticated tools […]

SecretSync, Security Layer To Protect Sensitive Files On Dropbox
The popular file synchronization and hosting service Dropbox encrypts all uploaded files and folders automatically to protect network snooping and other forms of attack and unauthorized access to those files. Dropbox recently […]
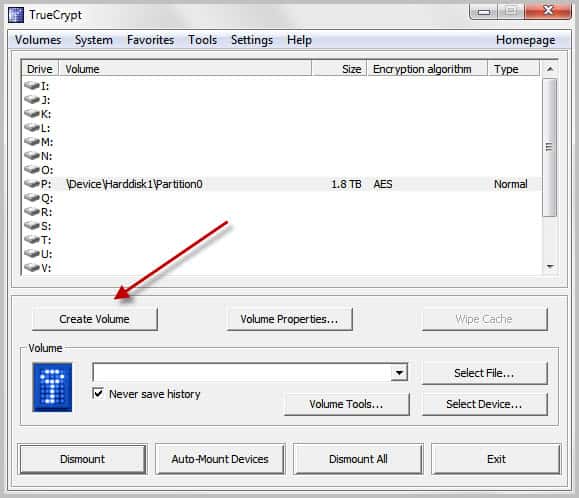
Storing Data In The Cloud With Dropbox And TrueCrypt
In Why You Need To Protect Your Data In The Cloud I have explained why it is important to protect data that you upload to the cloud. In this guide, I will […]
Why You Need To Protect Your Data In The Cloud
Several events recently have shown some of the weaknesses, or dangers, of cloud based hosting, and the need for information and guides to aid users in protecting their data in the cloud. […]
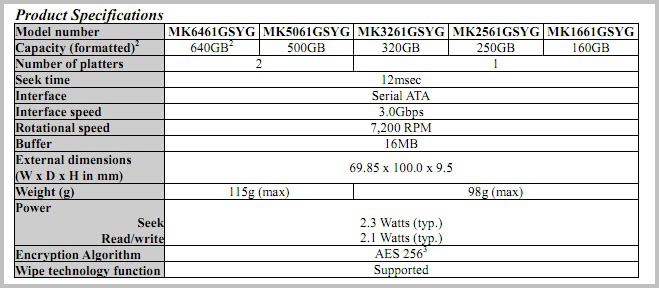
Toshiba Self-Encrypting Hard Drives With Host Authorization
The best way to protect data on one of your storage devices is to encrypt it. There are several free solutions out there, for instance by using the Open Source encryption software […]
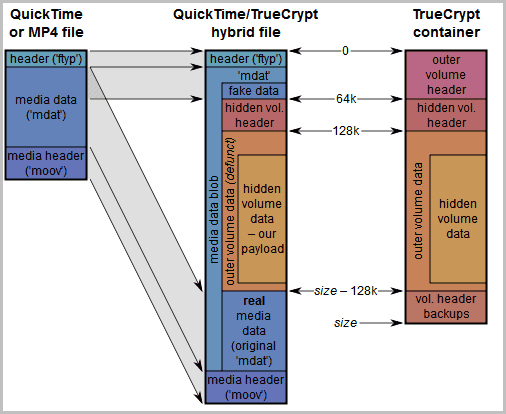
Disguising True Crypt Volumes In MP4 Videos
I have reviewed TCHunt yesterday, a free program to scan a computer system for unmounted True Crypt containers. The program can be used to prove the existence of an encrypted container on […]
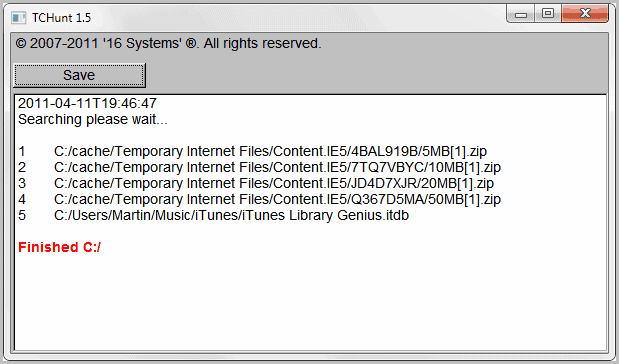
TCHunt, Search For TrueCrypt Volumes
TCHunt is a small portable application that can be used to find encrypted True Crypt volumes on the system. It has been specifically designed to demonstrate the possibility of finding True Crypt […]
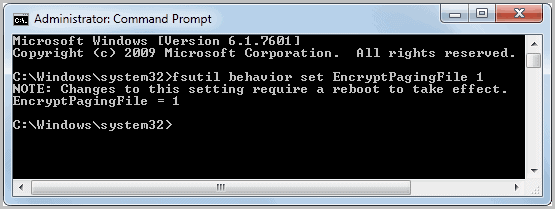
Encrypt Your Windows Pagefile To Improve Security
There is nothing better than encrypting the system partition and all other partitions if you want to protect your files from unauthorized access. There are still ways around this but they require […]
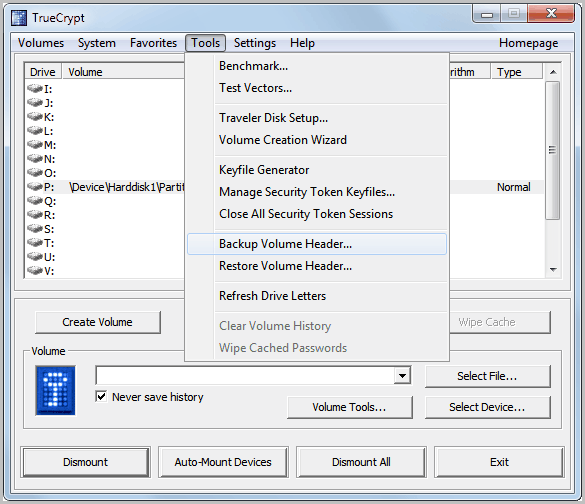
How To Backup True Crypt Data To Be Prepared For Emergencies
I have been using the encryption software True Crypt for years and ran only once into a situation where I nearly lost all the data on one of the partitions. Back then […]

Solid State Drives And Encryption, A No-Go?
Modern Solid State Drives are faster than their platter-driven brethren. They do have additional advantages like being completely silent when operating and better shock proof. The disadvantages are the high price per […]
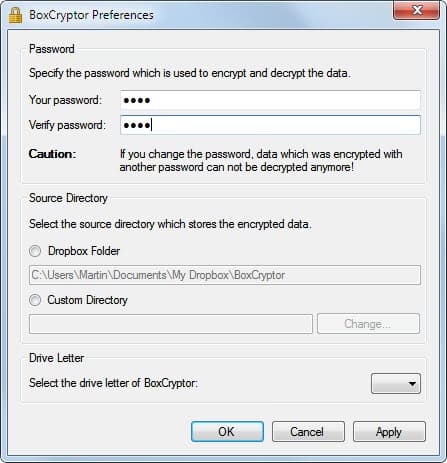
BoxCryptor: Dropbox and Co Realtime Encryption
BoxCryptor is a encryption software that encrypts cloud storage files and folders to protect them from unauthorized third-party access. Update: Boxcryptor is still available as a free service that users may use […]
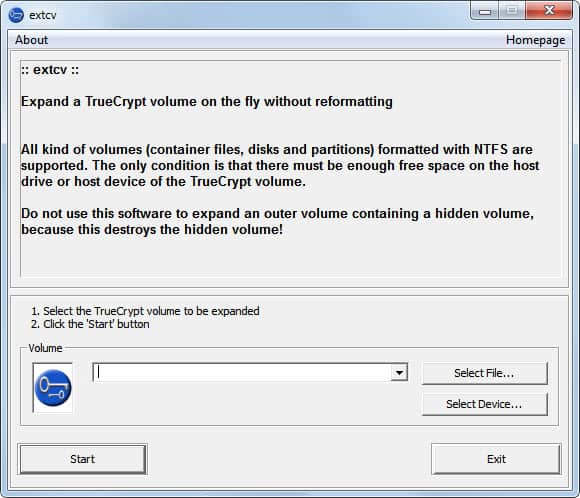
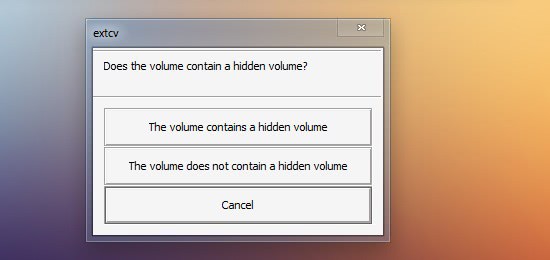
Resize TrueCrypt Volumes With Extcv
I have reviewed the open source tool Extcv back in July and came to the conclusion that it offered TrueCrypt users an elegant and unobtrusive option to resize the TrueCrypt volume on […]
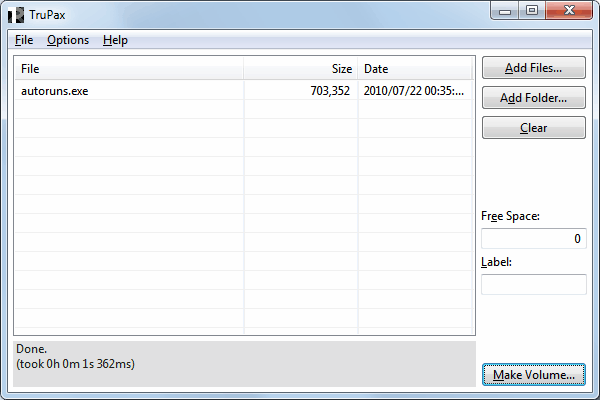
TruPax, Create TrueCrypt Containers Without True Crypt
It is not that complicated to create a TrueCrypt container, but it does take some time. You need the TrueCrypt software obviously to do that, and someone with admin rights to install […]

Essential True Crypt Tips
I have been working with True-Crypt for several years now, and like the open source program a lot. That much, that I'm still using it and not Microsoft's Bitlocker which is an […]
Increase Size Of True Crypt Container Instantly
Users of the encryption software True Crypt have the option to encrypt a full partition of a hard drive, or a container with a specific file size, say 20 Gigabytes. Problems arise […]
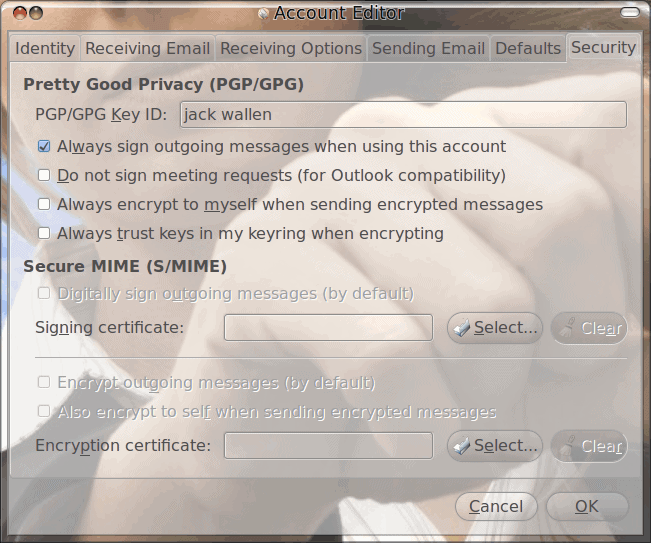
Encrypting email in Evolution
Evolution is an outstanding groupware suite with one of the finest email clients in all of Linux-land. For many users the standard email setup is great. It does everything they need: it […]
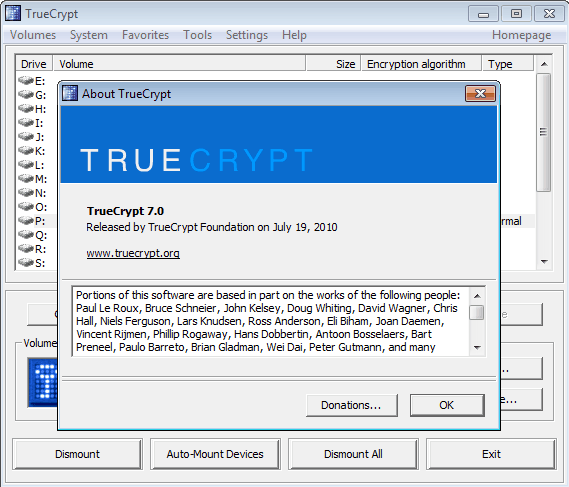
True Crypt 7.0, Adds Hardware Acceleration, Auto-Mounting
A new version of the encryption software TrueCrypt 7.0 has been released yesterday, as usual for Windows, Mac and Linux systems. The jump from version 6.3a to 7.0 is more than justified […]
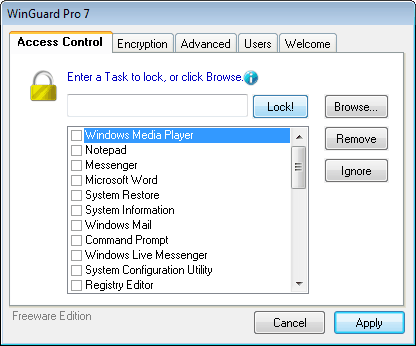
WinGuard Pro Free, Access Control And Encryption Software
WinGuard Pro is a security software with features such as program access control and data encryption. The free edition has a few limitations, more about that later in the review. The program […]

Password protect files and folders in Linux
Security sometimes equates to sanity. You have to keep sensitive information from prying eyes for various reasons. You might have a folder that needs to be given access only to certain people […]
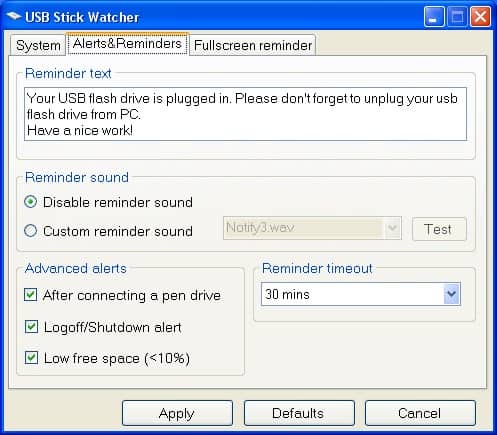
How To Protect USB Sticks And The Data On Them
Carrying an USB-stick around with you can be beneficial in numerous situations. USB devices are for instance ideal to copy data without having to carry a larger device like a notebook or […]
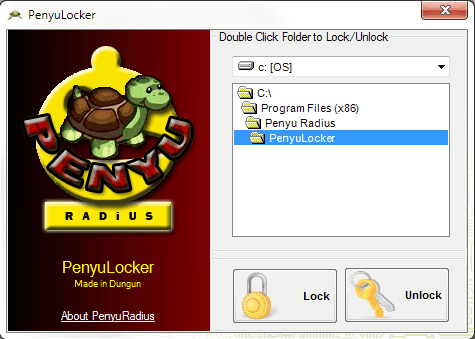
Password Protect And Disguise Folders With PenyuLocker
Encryption is the only option you have if you are serious about protecting data from unauthorized access. Programs like True Crypt or Microsoft's Bitlocker ensure that data is protected by a secure […]
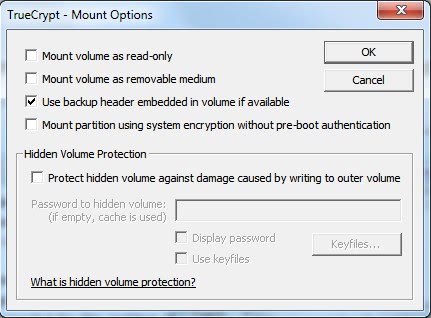
Incorrect Password Or Not A True Crypt Volume [Troubleshooting]
One of my True Crypt partitions failed to mount after a recent system crash. I entered the right password and received the message "Incorrect password or not a True Crypt volume". I […]
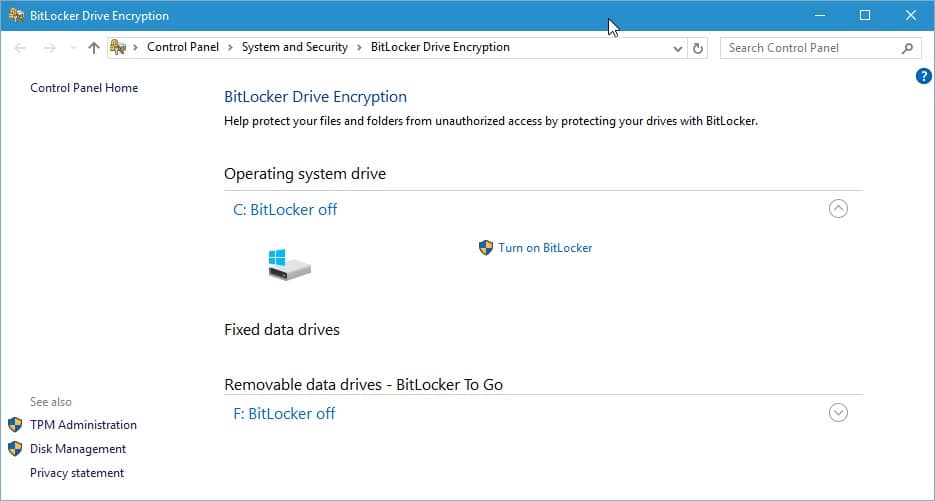
Bitlocker Encryption Not 100% Secure After All
Earlier this year a method to get access to data encrypted with the Open Source software True Crypt was published by security researchers. It involved physical access to the protected computer system. […]
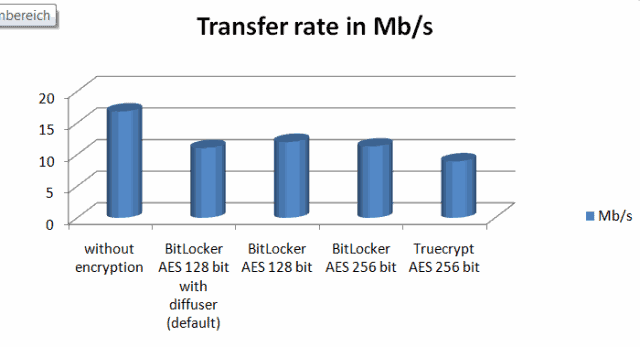
Bitlocker Versus True Crypt Performance
Alexander over at 4Sysops ran a benchmark comparison test of the encryption software programs Bitlocker and True Crypt on netbooks. Bitlocker is the encryption software that ships with Windows 7 Ultimate and […]
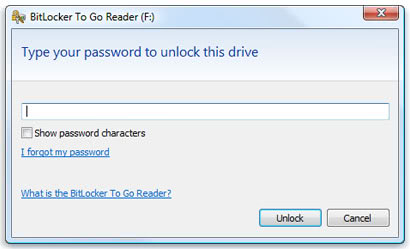
BitLocker To Go Reader
Bitlocker To Go is a program for Windows XP and Windows Vista that allows you to mount FAT Bitlocker volumes in read-only mode. Bitlocker is a data encryption technology that Microsoft implemented […]
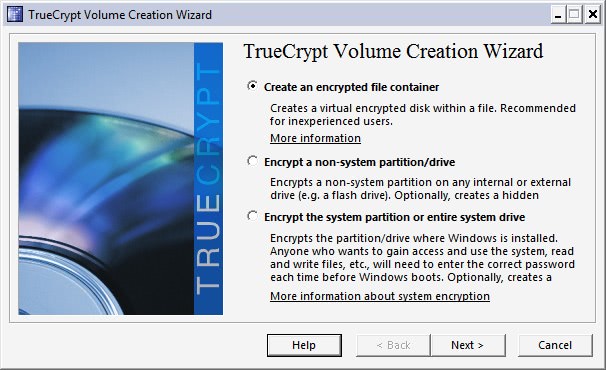
Disk Encryption Software TrueCrypt 6.3 Released
TrueCrypt is one of the most popular Open Source disk encryption software programs for the Windows operating system. It can be used to encrypt entire hard disks, partitions and to create encrypted […]

Add CryptKeeper for on-the-fly encrypted folders in Linux
You've more than likely read Martins' piece about the outstanding encryption tool Truecrypt "TrueCrypt 6.1 Released" and have used it to create easy to use, encrypted file systems on Windows machines. Of […]

Protect Data DVDs And CDs With Power Disk Lock
There are not many options to protect data on optical discs like CDs or DVDs. Probably the most common solution is to password protect or encrypt data so that it can only […]
How To Password Protect Data On CDs or DVDs
A recent comment here at Ghacks asked for help in finding a software program or solution to password protect CDs or DVDs. The following post explains how to password protect data on […]
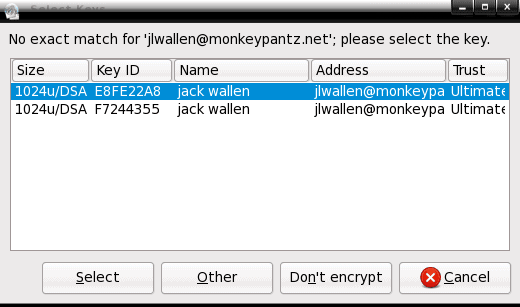
Encrypting email in Claws Mail
YACMA (Yet Another Claws Mail Article). Recently you may have taken a look at my Claws Mail articles: "Claws Mail: The unsung powerhouse email client." and "Claws Mail: Must have plugins." Hopefully […]

Recursively encrypt directories with gpgdir
Recently I wrote an article about Encrypting and decrypting files with GnuPG. This article described how to encrypt single files in with the help of gpg. But what happens if you have […]

Linux tips: Encrypting and decrypting files from command line with gpg
Are you paranoid? Are you afraid that someone is going to get ahold of data they sholdn't have? I am. And because of that I often encrypt files with a gpg key […]
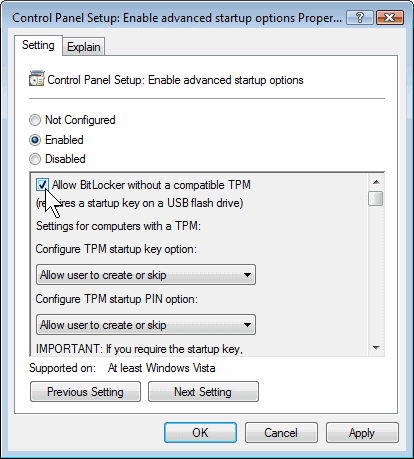
Enable Bitlocker On Unsupported Hardware
Bitlocker is an additional software component that got first distributed with Microsoft Windows Vista Ultimate and Enterprise, and with professional versions of newer Windows systems as well. It can be used to […]

Encrypting USB Devices Data With True Crypt
If you do not want to end like British government officials who lose USB devices with unencrypted data in front of pubs you might want to consider encrypting the data so that […]
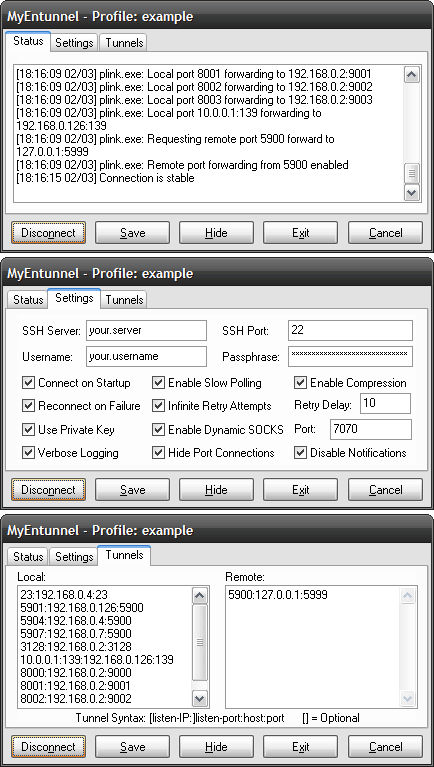
My Encrypted Tunnel
My Encrypted Tunnel is a basic System Tray application that can be installed as a Windows Service to establish and maintain TCP SSH tunnels. Here is a short explanation of what SSH […]

