Uncover File Manipulations With File Checksum Integrity Verifier
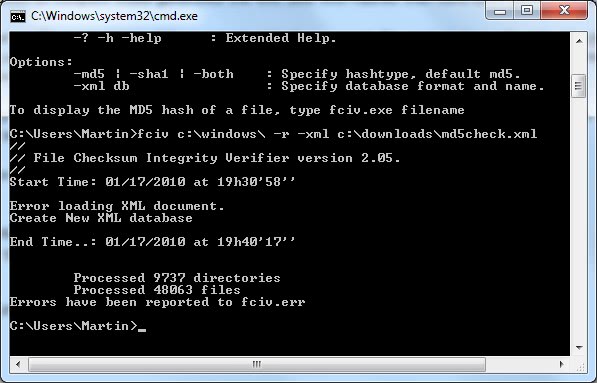
File Checksum Integrity Verifier is a free command line program by Microsoft that can be used to create and verify md5 checksums of files in a specific folder.
The program can for instance be used to check if files in a specific directory have been modified, which is often the case if malicious software has been executed on the computer system.
This is done by calculating hashes of every file - or only specific file types - in the selected directory with the option to compare those generated the first time with hashes that have been generated at a later time.
Identical hashes mean no file manipulation while nonidentical hashes suggest file manipulations. This does not necessarily mean an attack as updates may replace files as well and change their checksum in the process.
File Checksum Integrity Verifier
The File Checksum Integrity Verifier can be downloaded from the Microsoft homepage. The Microsoft Support page that lists the file download contains an explanation of the program's command line parameters.
The program needs to be unpacked after download. It is suggested to move the file fciv.exe into a system folder like the Windows folder so that it can be run without specifying a path but that is up to you.
MD5 hashes of a specific directory can be created with the following command:
fciv folder -r -xml output.xml
fciv c:\windows\ -r -xml c:\md5\20100117md5.xml
It is possible to specify file extensions with the -type parameter followed by the filetype, e.g. *.exe.
A previously created xml document containing hashes can be verified with the following command
fciv -v -xml output.xml
fciv -v -xml c:\md5\20100117md5.xml
The tool will display a list of modified files at the end of the comparison. It is possible to switch to use -sha instead of -md5. Users who want to verify the files regularly might want to consider creating a batch file for the file verification checks.
The tool can be very useful if you want to make sure that important files -- say files on a web server, documents, or program files -- have not been tampered with.
Update: Microsoft has removed the program from its servers, it is no longer available. You can check out the third party alternatives File Check MD5 or File Verifier++ which offer a similar feature set.
Update 2: And the tool is up again. You can download it from Microsoft with a click on the link in the summary below.

























obsolete part:
“Update: Microsoft has removed the program from its servers, it is no longer available”
Microsoft File Checksum Integrity Verifier download link :
https://www.microsoft.com/en-us/download/confirmation.aspx?id=11533
thanks for your fantastic blog. it contains all the info i need to take good decisions.
long life to ghacks!
Thanks so much for the information! I have updated the article so that the link is displayed again.
Just to let you know it is back on MS Servers and is working on Win Vista.
Also if you are a PowerShell user you may want to check ‘PsFCIV 2.0’ at the PowerShell File Checksum Integrity Verifier (PsFCIV) page (http://gallery.technet.microsoft.com/PowerShell-File-Checksum-e57dcd67).
Wow, I was just thinking about how I needed program something like this. Perhaps I don’t have to now. Thanks!
Didn’t know about this utility, thank you :)
In the past, I’ve used “ICE ECC” to verify integrity of files. It’s a program to create recovery data to repair damaged files, but it can be used to just check files for integrity (you can create recovery files that don’t contain recovery data; just integrity check): http://www.ice-graphics.com/
Be careful:
1) Product is unsupported.
2) Developing seems to be stopped.
3) Exclusions list (-exc parameter) doesn’t work at all.
I’ve found better solution – FCIV for PowerShell:
http://www.sysadmins.lv/content/scripts/PSFCIV_1.0.ps1
Hashtab (http://beeblebrox.org/)
Integrated in Windows Explorer ;-) but only on single files
The File Checksum Integrity Verifier is a good file, an excellent check. Unfortunately, per Microsoft, it is useful only on Microsoft Windows 2000, Windows XP, and Windows Server 2003.
worked fine on a Windows 7 test system.