Firefox will block insecure downloads soon by default
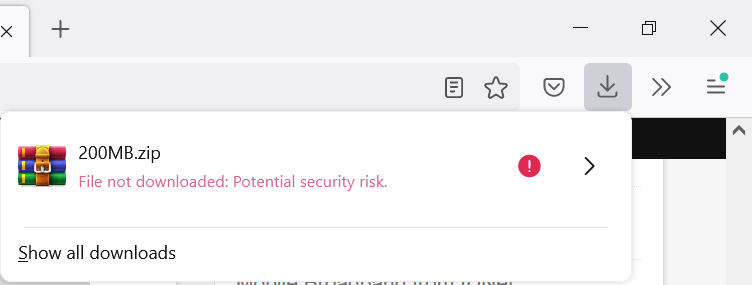
Mozilla's Firefox web browser will block the download of insecure files soon in mixed content environments.
Mixed content refers to sites using secure connections and insecure connections. Imagine the following scenario: you visit a secure site that is using HTTPS and start a download by clicking on a link. The linked resource is not on a HTTPS resource, but on a HTTP resource; this is what mixed content in the context of downloads refer to.
Files that are transferred via insecure connections may be tampered with, for instance by other actors on a network.
Firefox will block insecure downloads that originated from HTTPS sites soon, likely in Firefox 92, which will be released on September 7, 2021.
Firefox won't download the file in this case automatically; the browser displays a warning in the download panel -- File not downloaded. Potential security risk -- with a red exclamation mark icon.

A click or tap on the download in the panel opens additional information and options.
Firefox users may allow the download using the prompt that opens or remove the file.
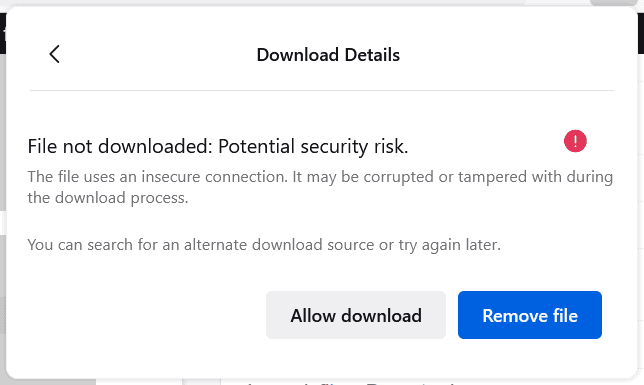
The blocking happens only because of the insecure connection, not because the file has a virus or other unwanted content. It may still be a good idea to run the file through a virus scanner or service such as Virustotal to make sure it is clean and likely without danger.
Firefox 92 comes with a preference switch that controls the behavior. It can be turned off to restore the previous downloading behavior:
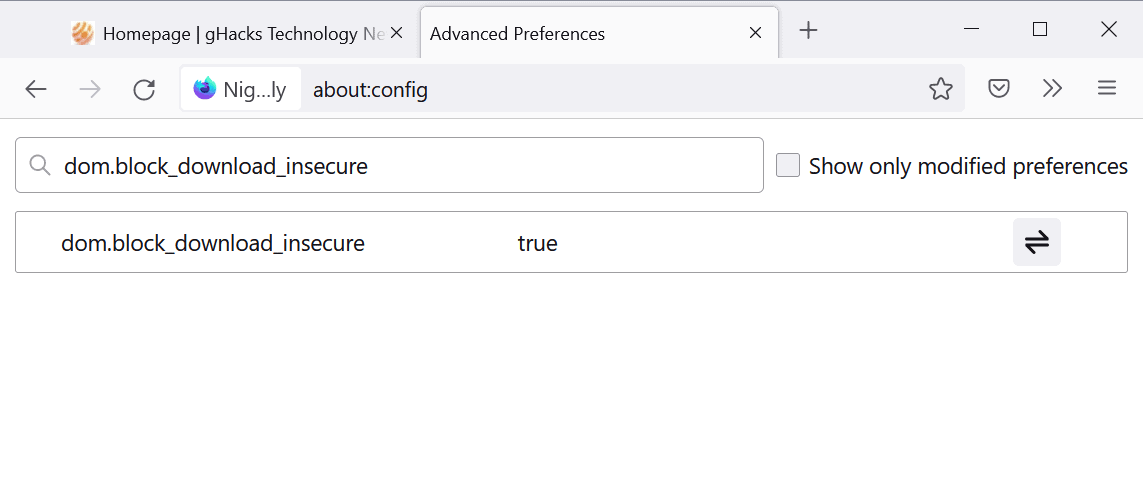
- Load about:config in the Firefox address bar.
- Confirm that you accept the risk.
- Search for dom.block_download_insecure.
- Use the toggle icon to set the value to
- TRUE: to keep the security feature enabled.
- FALSE: to disable the security feature.
Mozilla notes that about 98.5% of all downloads in Firefox Nightly use HTTPS. In other words: 15 in 1000 downloads will be blocked once the change lands in Firefox Stable, provided that the percentage value is about the same.
Google introduced the blocking of downloads in an insecure context earlier this year in Chrome 86. Most Chromium-based browsers block downloads from HTTP sources if the originating page uses HTTPS. Chrome displays a notification in the download panel if a file cannot be downloaded because it originates from a HTTP server. Chrome users may discard or keep the download, similarly to how Firefox handles these downloads.
Closing Words
HTTP downloads that originate on HTTPS pages will be blocked by default; users do have the option to override the blocking and to disable the security feature entirely.
Now You: what is your take on the feature? Good addition? (via Techdows)





















Had to go into about:config to disable this.
Once again…I am a BIG BOY…
STOP DOING THINGS FOR MY OWN GOOD.
I have Microsoft Defender breathing down my neck, I have all the rest of their defense garbage breathing down my neck.
Then I have my web browser breathing down my neck as well as everything else.
LEAVE ME ALONE already!!!!
I get into my Toyota and it has to tell me to drive safely after beeping because I haven’t put my seat belt on yet.
My phone tells me that my volume is too loud.
My Microwave oven has to consistently tell me that my food is ready.
Everything has to either beep, flash or send me text message.
If I worked on the Starship Enterprise Bridge I would take a phaser to every last one of them on that ship because of the constant beeping and flashing lights.
Enough already because you are doing nothing but polluting everyone’s life with unnecessary nonsense.
This crap is supposed to be disabled because I disabled it myself in the preferences and now it turns out that these idiots add one more option that can’t even be disabled easily and they end up messing up my unique download link.
>Personally, I still visit gHacks once in a while, but I’ve noticed that I visit it less and less as time progresses, and the useless and mindless ranting of trolls continues.
Sorry no one will worship you. No one cares whether you visit this site or not, do you care what color of socks I wear? My favorite band? What is this, AOL? LOL!
I agree. This Geoff fellow accuses others of trolling but comes off as a troll himself. I dislike the aggressive tone Iron Heart constantly takes, but he (or she?) is not a troll, just a person with an opinion. The posts from Geoff here have just gone over the top with bizarre accusations, and we’re now meant to feel sorry that he dislikes gHacks…
Too much drama altogether. I’m going to take a break from my computer.
This Iron Heart troll is filled with hate and anger. Sad.
And gHacks is more than willing to publish this troll’s rage, unsubstantiated claims, and attacks. So I’m sure they will have no problem publishing my simple reply.
1. “You are not supposed to use that word like some racist bigot…”
You are implying I am a racist. I am not, and your implication is offensive. You sound like one of those racist bigots who is trying to deflect their shame.
2 .”Really says it all, it’s not about what is best for the regular user, rather, as with everything else in life, it is about power and control.”
I mentioned nothing about power and control. I don’t care about power and control. I actually gave up my powerful management job to work for a non-profit charity that feeds the homeless. You clearly have a hateful agenda and are putting words into other people’s mouths. Firefox is excellent for the average user as well as power users.
3. “It speaks volumes about the Firefox community when people see them hating on fellow privacy projects.”
I am a single user. I do not represent the Firefox community (nor Mozilla). But it is a well-documented behavior of racists to view the acts of a single individual as representative an entire community. Only one of us is filled with hate and is acting in a hateful way, and it’s clearly not me. You attacked me with your hostile words (which gHacks was willing to publish), and I never even thought of mentioning or referencing you (or anyone else) in any way in my post.
4. “Thank you for revealing the true face of the FF community here.”
Again, I am a single user. I do not represent the Firefox community. But, regarding your comments, it is common for a racist to view the world as unified groups of people who hate each other. Personally, I don’t hate anyone. You would likely benefit from some quality therapy that could help you get out of your hate-filled world. Life is much simpler and honest when you stop hating others and stop blaming others for your hate.
If you look at Iron Heart’s well-documented history, he’s clearly just another one of those angry far-right hateful people. Firefox is an excellent project developed by an organization trying to foster equality. This clearly angers him so much that he has literally spent hours of his time writing hundreds of rants on gHacks and elsewhere. The tone, content, hostility, and hate is always the same, so it’s easy to spot his writing anywhere. It’s like a broken record. Nothing new to say, and no signs of growth.
I do understand, however, why he spends so much time posting his rants here on gHacks. He has explained that he has been banned for inappropriate conduct on other sites (although people like that rarely have much insight into why their conduct is inappropriate). That speaks volumes on its own.
gHacks obviously hopes to profit from allowing his rants (just like CNN and Fox News try to profit from wild broken-record rants), although I have read multiple threads on other sites where people have disclosed that they no longer visit gHacks because they are tired of all the obvious trolling interfering with valuable and helpful discourse. Personally, I still visit gHacks once in a while, but I’ve noticed that I visit it less and less as time progresses, and the useless and mindless ranting of trolls continues.
Absolutely disgusting post. Wow! It is clear you are a homophobe, and also a racist, and frankly it is disgusting. Why does Martin let this abhorrent filth on this site?
@Geoff Williams
> This Iron Heart troll is filled with hate and anger. Sad.
Your original post reads like a troll reply, because it is one. Any further allegation of me being a troll coming from you (of all people) will thus be discarded.
> You are implying I am a racist.
If the slave word is the first rhyme you have for Brave, what else I am supposed to think?
> You sound like one of those racist bigots who is trying to deflect their shame.
Your kitchen psychology is failing you here. There is no indication of racism in any of my posts.
> I mentioned nothing about power and control. I don’t care about power and control.
You are hating on fellow privacy project. Is that in the best interest of users? Nope. What you do only makes sense if you are a fanboy with an agenda, sprung from a toxic community fighting for its relevance. Or you are completely irrational and don’t know anymore what you say. Choose one.
> You clearly have a hateful agenda and are putting words into other people’s mouths.
I don’t think so. And considering your original troll post, I have no reason to put words in your mouth.
> I am a single user.
Then why are you drones so exchangeable? Your hate always goes in the same direction, your non-arguments are also the same. If you want to be seen as not being a drone, try something more original.
> But it is a well-documented behavior of racists to view the acts of a single individual as representative an entire community.
Hey slave-rhymer, what makes you think I am a racist? Any kind of actual proof?
> You attacked me with your hostile words (which gHacks was willing to publish), and I never even thought of mentioning or referencing you (or anyone else) in any way in my post.
Your original post was filled with trolling and was bait. People are not blind, your post is still there, one can read it.
> You would likely benefit from some quality therapy that could help you get out of your hate-filled world.
And you would likely benefit from having some actual argument that is more than trolling or whining. My “therapy”, as in, the wellness I would need, would be you stupid drones leaving or coming up with something more original.
> If you look at Iron Heart’s well-documented history, he’s clearly just another one of those angry far-right hateful people.
Source: Your ass.
If people took a look at my history, they would find that I am one of the more apolitical commenters here.
> Firefox is an excellent project developed by an organization trying to foster equality.
I don’t know what Mozilla fosters other than their CEO’s paycheck (while at the same time firing 250 people amidst a pandemic), so much for “equality”. Also, only 3% want to use their product despite the fact that it can be downloaded for free. Do I need to explain why, or do you already know why?
> Nothing new to say, and no signs of growth.
What do you expect when you have me deal with the same old, retarded shit once again? I will post a more original reply once you drones come up with a more original argument.
> I do understand, however, why he spends so much time posting his rants here on gHacks. He has explained that he has been banned for inappropriate conduct on other sites (although people like that rarely have much insight into why their conduct is inappropriate). That speaks volumes on its own.
Complete lie. I have never said that I have been banned anywhere, simply because I am not anywhere else. I can’t be banned from where I was not present in the first place. Also, fabricate your lies a bit better next time:
1) I am spending so much time here dealing with trolls like you that I would hardly have the time to do the very same thing anywhere else. Tech news isn’t my whole life, and the day only has 24 hours.
2) If I had been banned anywhere, it wouldn’t make much sense for me to openly admit it, would it? Duh…
> gHacks obviously hopes to profit from allowing his rants (just like CNN and Fox News try to profit from wild broken-record rants), although I have read multiple threads on other sites where people have disclosed that they no longer visit gHacks because they are tired of all the obvious trolling interfering with valuable and helpful discourse.
Source for people leaving gHacks? Or are you just being, let’s say, “creative with the truth” again? I don’t know what Martin’s motivation is for allowing comments other than them not violating the gHacks comment guidelines… Anyway, your hopes for censorship won’t be fulfilled here. Don’t even bother. This goes both ways, by the way. gHacks also allowed YOUR trolling and YOUR lies to be published after all. Am I supposed to whine about that, just like you?
> Personally, I still visit gHacks once in a while, but I’ve noticed that I visit it less and less as time progresses, and the useless and mindless ranting of trolls continues.
So you’ve concluded that, when you visit once in a while, that the best course of action would be to become a low effort troll? OK.
I am done here. Enough time wasted on the lying troll.
jesus christ learn to be more succinct
This is a much better implementation than Chrome or any of the Chrome wanna-be browsers like the one that rhymes with “slave”.
Mozilla is letting users know about a potential issue and treating them like adults by giving them the choice to still download the file if they want. And if Firefox users don’t want to even be warned, there is a setting to control that too. Perfect.
Now we just need to convince the thousands of software developers (including, ahem, Microsoft) that distribute software via HTTP to finally switch to HTTPS. It’s shocking that in this day and age that about 3-5% of software developers still distribute their software on pages that only allow HTTP connections. HTTPS certificates are literally free now, so there is no excuse except laziness to not use HTTPS.
@Geoff Williams
> This is a much better implementation than Chrome or any of the Chrome wanna-be browsers like the one that rhymes with “slave”.
You are not supposed to use that word like some racist bigot, Mozilla has spent good money to remove it entirely from Build Bot: https://forums.escapistmagazine.com/threads/mozilla-gives-15k-to-remove-slave-from-build-bot-documentation.138153/
Apart from that, it speaks volumes about the Firefox community when people see them hating on fellow privacy projects. You guys hate Brave much more than you do Chrome and Edge, browsers that actually violate user privacy. Really says it all, it’s not about what is best for the regular user, rather, as with everything else in life, it is about power and control. Thank you for revealing the true face of the FF community here.
> Mozilla is letting users know about a potential issue and treating them like adults by giving them the choice to still download the file if they want.
So does any other browser implementing that feature, this is not unique to Firefox.
> And if Firefox users don’t want to even be warned, there is a setting to control that too. Perfect.
In what kind of reality is that “perfect”, my dude? If a download of yours triggers a warning in the first place, there usually is something more to the story. One can make conscious exceptions already, no point in lowering security standards even further by disabling the warning(!).
Still miss FlashGot, now I have to use VideoDownloaHhelper and DownloadWithJDownloader (plus native application) to compensate for it.
Oh! While I was wasting my time with userchrome after 91 release I didn’t see this ‘improvement’ on search bar: https://postimg.cc/yWf061mZ
Good thing I use IDM for my downloads. If I want to download an app or a zip file that Firefox doesn’t approve of then I will use another browser. They are not my parents? No wonder Firefox is loosing clients left and right.
That’s why I always enjoy using wget, not a browser nor their extensions for downloads.
So about 1 out of every 67 downloads.
You can not call yourself a private browser if your default search engine is Google.
Will Microsoft take note of that I wonder? After all, all downloads from the Microsoft Catalog Site take place over an insecure link.
Good. Current Firefox 91 already has ‘dom.block_download_insecure’ in about:config, but set to false given it’s planned.
Here with HTTPSEverywhere set to ‘Encrypt All Sites Eligible’ it won’t change much. I don’t use Firefox’s HTTPS-Only mode given I’ve encountered at least one site where setting an exception just wouldn’t work : [http://www.les-verbes.com/]. HTTPSEverywhere is far more elaborated IMO.
As always or almost this new ‘Block insecure downloads’ feature has it’s option in about:config, cherry on the cake.
Switch three unchanged prefs of security.mixedcontent, two of which mentioned in user.js for blocking http content and one additional for upgrading passive resources. So that will be another layer of dealing with http sites along with Https Everywhere. Prefs will work on all sites to do its best, while add-on will work on sites present in its database. The next best solution after Https only mode.
@Yash,
> “[…]while add-on will work on sites present in its database” : HTTPSEverywhere set to ‘Encrypt All Sites Eligible’ (EASE) blocks systematically all non-HTTPS connections, as Firefox’s ‘HTTPS-Only’ mode. This approach, given it allows exceptions, is far more convenient than a ‘security.mixed_content.block_display_content’ set to true because there may be HTTPS sites where connections to non-HTTPS servers are considerd by the users as being worth it.
Nevertheless in any case ‘security.mixed_content.block_active_content’ remains set to true (default).
In my case, I use several HTTPS Web radio portals which call different non-secure Web radios : setting ‘security.mixed_content.block_display_content’ to true would block access to these 3rd-party servers. HTTPSEverywhere, in EASE mode, can be instructed to apply exceptions, bringing the best to one equation.
“because there may be HTTPS sites where connections to non-HTTPS servers are considerd by the users as being worth it.” For this, the first two prefs of blocking are out, but maybe third pref of ‘upgrading display content’ can be a potential solution as it will not block http but rather *try* to upgrade passive resources to https if it can on https sites(http sites load just fine with all three prefs switched) atleast that’s what its name suggest.
I don’t use https-only mode and also no https everywhere. I use these three prefs and my thinking was – there will no http content on https sites, plus http ones will load just fine without having to set exceptions and encounter all sorts of warning, like the site you mentioned above load just fine. But this point – “I use several HTTPS Web radio portals which call different non-secure Web radios” – has got me thinking there are other scenarios as well and time has come to review few things. Maybe you can check if third pref helps with this, IOW doesn’t block http but just try to upgrade it, and share the result here.
@Yash, all this is quite complex.
> “[…]maybe third pref of ‘upgrading display content’ can be a potential solution[…]”
This is the “security.mixed_content.upgrade_display_content” pref, but to work the user must have set “security.mixed_content.block_display_content” to true as well otherwise if the attempt to connect to 3rd-party sites via HTTPS fails, the connection won’t return to HTTP …
I’ve used these combinations in the past, found them in archives :
// attempt to load mixed content that is optionally blockable from HTTPS domains instead of the referenced HTTP domains
// REQUIRES SAME VALUE AS “security.mixed_content.block_display_content”
// pref(“security.mixed_content.upgrade_display_content”, true); // Default=false
This is why an HTTPS-only mode (that of Firefox or that of HTTPSEverywhere) with exceptions appeared to me as the simplest approach:
// Enforce enabling insecure active content on https pages – mixed content
pref(“security.mixed_content.block_active_content”, true); // DEFAULT=true
// Enforce disabling insecure passive content (such as images) on https pages – mixed context
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
The only switch from there on is an HTTP exception at the discretion of the user. HTTPSEverywhere can set the exception for once or register it. No fuss, no problem, best security/freedom ratio IMO.
You mixed enabled and disabled there on last two prefs which proves you’re….human. Don’t get me wrong, https-only mode with exceptions or https everywhere with EASE mode are the best, but those are for https sites. The security.mixed prefs kick in exceptions mode as https everywhere or https-only mode are the first checkpoint. Those three prefs are always inferior to these two as they don’t deal with scripts, just passive resources.
security.mixed_content.upgrade_display_content works independently of security.mixed_content.block_display_content pref. In browserleaks.com/ssl – if I switch block pref, result will be ‘blocked’ in all six categories, in upgrade pref it will be ‘upgraded to https’ in first three and blocked in last three, same if both block and upgrade are enabled. In https-only mode or in EASE mode, ‘upgraded to https’ in all six categories.
But that’s all sort of theoritical. I just want to know one thing, if you only switch upgrade pref to true, with EASE mode or https-only mode but that will not matter when setting an exception, will some https sites as you said need http content load properly?
I would have “mixed enabled and disabled there on last two prefs”? Where?
// Enforce enabling insecure active content on https pages – mixed content
pref(“security.mixed_content.block_active_content”, true); // DEFAULT=true
// Enforce disabling insecure passive content (such as images) on https pages – mixed context
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
Nothing mixed here. Please explain.
> “security.mixed_content.upgrade_display_content works independently of security.mixed_content.block_display_content pref”
Yes and no. If the former is enabled, an http connection to a 3rd-party server will attempt to connect via https, but if it fails AND the latter is disabled, there will be no return to http.
> ” I just want to know one thing, if you only switch upgrade pref to true, with EASE mode or https-only mode but that will not matter when setting an exception, will some https sites as you said need http content load properly?”
Could you please explain, I’m afraid I don’t understand your question.
Mea culpa (3 times. Erratum! Now, back to English : atchoum, I made a big mistake.
@Yash, when you write “security.mixed_content.upgrade_display_content works independently of security.mixed_content.block_display_content pref” you are right. %y fault.
To summarize the three mixed-content prefs :
// disable (true) or enable (false) insecure active content on https pages – mixed content
pref(“security.mixed_content.block_active_content”, true); // DEFAULT=true
// disable (true) or enable (false) insecure passive content (such as images) on https pages – mixed context
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
// disable (false) or enable (true) insecure passive content UPGRADE (such as images) on https pages – mixed context
// When enabled, this preference causes Firefox to automatically upgrade requests for media content from HTTP to HTTPS on secure pages.
// The intent is to prevent mixed-content conditions in which some content is loaded securely while other content is insecure.
// If the upgrade fails (because the media’s host doesn’t support HTTPS), the media is not loaded.
pref(“security.mixed_content.upgrade_display_content”, false); // DEFAULT=false
This is where I made the mistake : If the upgrade fails (because the media’s host doesn’t support HTTPS), the media is not loaded… EVEN IF “security.mixed_content.block_display_content” is false (default).
A long time mistake which missed being corrected (reason, not excuse!) given I use HTTPSEverywhere in EASE mode and therefor have left all three above-mentioned prefs to their default values.
Mixing part has been cleared in your last comment, I misunderstood it for something else previously, my mistake.
Yeah I also used EASE mode in https everywhere and switched to https-only mode when it first came out. But in your original comment you mentioned a site which doesn’t work in https-only and so I disabled it for now. Then I went on to see some other prefs who can cover atleast some functionality, which were these three prefs, the site you mentioned load perfectly, so I thought okay new settings for now. But this line – “I use several HTTPS Web radio portals which call different non-secure Web radios : setting ‘security.mixed_content.block_display_content’ to true would block access to these 3rd-party servers.” That has got me thinking again, coz first that is a valid point, block pref would stop that thing, so here’s my question? Instead of block pref being turned on, how about switch upgrade pref, leave block to default, and see if problem remains the same.
If the problem is still there, I definitely will switch to https everywhere and EASE mode, and leave these prefs as they are, as add-on can be configured for individual sites but prefs can’t.
@Yash, to answer your question:
pref(“security.mixed_content.block_active_content”, true); // DEFAULT=true
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
pref(“security.mixed_content.upgrade_display_content”, true); // DEFAULT=false
Now open : [https://vtuner.com/setupapp/guide/asp/BrowseStations/startpage.asp]
Select a radio. Vtuner will (try to) connect to the radio’s server and most likely radio won’t start (unless the sever accepts HTTPS, seldom with radio servers). Try/test different scenarios ..
>>>”Vtuner will (try to) connect to the radio’s server and most likely radio won’t start (unless the sever accepts HTTPS, seldom with radio servers).”
Depending on the capabilities of the streaming server and the associated client – in your case jPlayer, streaming audio is in principle be transmitted via the common HTTP protocol.
Known as HTTP Streaming, a push-style data transfer technique that allows a web server to continuously send data to a client over a single HTTP connection that remains open indefinitely. Technically, this goes against HTTP convention, but HTTP Streaming is an efficient method to transfer all kinds of dynamic or otherwise streamable data between the server and client.
>>>”and most likely radio won’t start”
… because there is no stream at the moment,
… the webmaster has inserted the streaming URL sloppily and incorrectly
… YOU have this problem caused by a completely unnecessary messing around with browser settings that you obviously don’t understand.
>>>”Try/test different scenarios ..”
Test a typical HTTP Streaming in your browser’s native player:
http://listen.011fm.com:8020/stream11
Note the Port 8020, if that’s blocked by your firewall … no stream.
Via port 443 (HTTPS) proxy
https://usa6.fastcast4u.com/proxy/wsjfhd?mp=/1
The Proxy 443 link enables listeners to tune-in even if they use firewalls that may block listening to Online Radio streams.
Thanks for listening ;~)
@Emil Brausewetter, I listened and I heard (an ad proclaimed ‘You’ll see what you hear’ and here it’s the opposite : I heard what I saw/read!)
Your comment is very technical. All I meant to say is not that I don’t receive radio streams from vTuner (or elsewhere) because I do!. Only that vtuner itself is HTTPS but it calls radio streams via HTTP and if I either,
Block Display Mixed Content is true :
pref(“security.mixed_content.block_display_content”, true); // DEFAULT=false
or Allow Display Mixed Content Upgrade is true
pref(“security.mixed_content.upgrade_display_content”, true); // DEFAULT=false
then the connection to the HTTP-only radio streams will fail.
In fact it’s all in dealing with three Mixed-Content prefs, the third ((“security.mixed_content.upgrade_display_content”) finally unworthy, perhaps the reason wwhy Firefox left it as ‘false’
What you (and this artikel) seem to fail to notice is the distinction between
mixed passive/display contentandmixed active content.For further information I recommend the following article:
https://developer.mozilla.org/en-US/docs/Web/Security/Mixed_content#types_of_mixed_content
By default, Firefox does not block “mixed passive/display content”, the threat is lower. No point in flipping the pref
security.mixed_content.block_display_contentunless you are truly paranoid.In your scenario
Tom Hawack said on August 17, 2021 at 9:46 am
only this two settings are relevant for “mixed passive/display content”, in case of “vtuner.com” the audiostream.
pref(“security.mixed_content.block_display_content”, false);// DEFAULT=falsepref(“security.mixed_content.upgrade_display_content”, true);// DEFAULT=falseYour observation “most likely radio won’t start (unless the sever accepts HTTPS …)” is in complete contradiction to the settings you specified:
1. setting = Allow passive/display HTTP content – the radio should start streaming
2. setting = upgrade_display_content=true – makes no sense at all because HTTP is allowed and if the stream is delivered via HTTPS, this settings are ignored anyway.
Because of this muddled nonsense, I could not resist and dared to point out possible other causes as well:
… streaming server offline
… the webmaster has inserted the streaming URL sloppily and incorrectly
… ports blocked
… services at OS level disabled and so on.
Take it sporty …
@Emil Brausewetter, taking it “sporty” would mean a quest of reputation?! No ego as far as i’m concerned, if I can help I try, if I mistake then always happy to learn. No leadership battle! I’m betting on your natural humbleness :)
This said, seems to me that the distinction between mixed-display and mixed-active is clearly established; this is not what we’ve been debating about in this thread.
The whole point here above was to consider how an HTTPS site calling HTTP 3rd-party servers would perform when considering blocking mixed-display and, further on, considering mixed_content.upgrade_display_content.
It has NOT been mentioned that Firefox by default blocks “mixed passive/display content” : on the contrary I have repeated more than once the default prefs’ values. Be repeated again in case you would have missed it :
pref(“security.mixed_content.block_active_content”, true); // DEFAULT=true
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
From there on Yash mentioned the 3rd option :
pref(“security.mixed_content.upgrade_display_content”, [true/false?]); // DEFAULT=false
We then debated on this latter pref and concluded that, if set to true AND an HTTPS site called an HTTP 3rd-party that refused HTTPS, then the connection would fail EVEN IF security.mixed_content.block_display_content was left at ‘true’ (DEFAULT).
So, obviously, it’s not that we disagree but that you haven’t understood or that I’ve insufficiently explained. Maybe a drawing would have helped.
>>>”taking it “sporty” would mean a quest of reputation?!”
Nonsens! It means: Fair Play.
Anyway, I’ve had some time lately to check out your scenario:
pref(“security.mixed_content.block_display_content”, false); // DEFAULT=false
pref(“security.mixed_content.upgrade_display_content”, true); // DEFAULT=false
You are right, so I apologize for the NONSENS I said in this paragraph
Quote:
“Your observation “most likely radio won’t start (unless the sever accepts HTTPS …)” is in complete contradiction to the settings you specified:
1. setting = Allow passive/display HTTP content – the radio should start streaming
2. setting = upgrade_display_content=true – makes no sense at all because HTTP is allowed and if the stream is delivered via HTTPS, this settings are ignored anyway.”
mea culpa, mea culpa, mea maxima culpa […]
It feels so better when some random folks debate on something without rants or false arguments, Chef’s kiss.
Thanks for the link, definitely one to be bookmarked.
It didn’t load with upgrade pref. Tried different scenarios and none worked. Looking back at it I was naive, as in the browserleaks test http content gets blocked, hence url remains https irrespective of results. I should’ve seen this earlier. Now back to EASE mode with a bit of nostalgia.
@Yash, life is adventure, computing an odyssey :=)
Microsoft update catalog uses HTTP to serve the files and so do many other common place services
Only if they had this much energy to work towards fixing ten year or older bugs in bugzilla.
A lot of downloads are one time generated per session, so in that case HTTP downloads can’t be generated back from webpage after it fails initially.
Alienating users is an art and FF mastered is well.
You clearly didn’t read article properly, plus in screenshots there is allow option, so one time download thing is nonsense.
I literally found this article via Google because Firefox blocked my download, and when allowing the download it would fail because Firefox tries to restart it or something, but the link was one-time only. Next time download the beta and try it before spreading bs. Such a ridiculous “feature”…
Thanks, but point was everything that was said in original comment is already covered in article. Plus it has not landed in stable release yet, so some *issues* will get resolved, like in every other software. Restart or something like that, maybe that’s down to release channel you selected, in beta though some things can break, hence its called beta.
At least they are handling this better than Chrome where if you download something insecure, nothing really happens so you can’t even know if the download has been blocker or for what reason, you don’t know what’s happened unless you’ve read the patch notes that this function is now available and running inside the browser.
if you download something insecure in Chrome you get notification the download is blocked
or you get notification to run the file in virustotal and download.