Is Mozilla's new DNS feature really dangerous?
A story on the Ungleich blog claims that Mozilla integrating two new DNS related security and privacy features into Firefox is dangerous.
The two features discussed in the opinion piece, DNS over HTTPS and Trusted Recursive Resolver are available in Nightly builds of the web browser currently.
We talked about DNS over HTTPS when Mozilla revealed it to the public back in March 2018 and published a guide to enable DNS over HTTPS in Firefox.
DNS is used to convert host names and domain names to IP addresses. The request is sent to a server which returns the IP address so that the connection can be established.
Firefox uses the default system DNS service by default which often is provided by the Internet Service Provider unless it has been changed by the user or an administrator.

With DNS over HTTPS and Trusted Recursive Resolver enabled, Firefox would use the DNS service configured in the browser and not the one on the system anymore.
The author of the article identified two core issues with the implementation:
- That the system is not opt-in but opt-out.
- That a third-party, in the case of the current implementation Cloudflare, gets access to all DNS requests of all Firefox users (based on 1)
While it is certainly true that Mozilla would like to enable the functionality for all of its users eventually, it is not the case right now.
The feature is only available in Firefox Nightly at the time of writing. Nightly is a development version of Firefox that gets multiple updates every week; it is not intended for production environments and features that land in Nightly may or may not land in Firefox Stable.
It is true that Mozilla runs a Shield study but it is opt-in according to Mozilla. It is possible that the whole system won't be opt-in when (if) it is launched in Firefox Stable.
Mozilla signed a deal with Cloudflare for the test. Cloudflare agreed to even stronger privacy terms. There is no indication that Cloudflare will be the sole provider (or a provider at all) that Mozilla works with when it is launched in Firefox Stable.
If that would be the case, it would certainly be problematic from several points of view:
- Single point of failure: if Cloudflare goes down, down goes the ability to browse the Internet.
- Cloudflare is a U.S. company and a third-party.
Closing Words
Nightly is not Firefox Stable and it should be clear that Nightly's main purpose is to test new features and changes. While it may be possible at times to look at features that Mozilla plans to move to Firefox Stable, it is sometimes not that easy and it appears that this is the case with DNS over HTTPS and Mozilla's test that it run on the Nightly channel.
It would certainly be an issue if Mozilla decided to include the feature in Firefox Stable and make it opt-out and use Cloudflare as the sole company to provide DNS lookups. I think that it is very unlikely that this is going to happen as it would open a can of worms.
It is already possible to run custom DNS over HTTPS servers and Firefox's current implementation allows custom addresses to be used.
In other words: it is too early to come to a conclusion.
Now You: What is your take on this?




















I just noticed the latest Tor Bundle Browser aka TBB 13.5.3 (based on Mozilla Firefox 115.15.0esr)
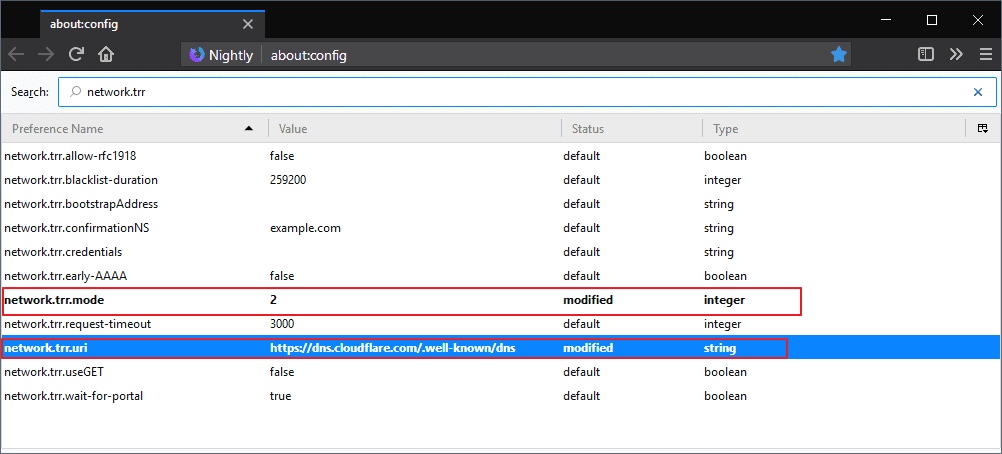
have disable it, going to about:config and looking up network.trr.mode it is set to 5, which means it is disabled.
https://wiki.mozilla.org/Trusted_Recursive_Resolver
DNS-over-HTTPS (DoH) allows DNS to be resolved with enhanced privacy, secure transfers and comparable performance.
The resolver mode. You should not change the mode manually, instead use the UI in the Network Settings section of about:preferences
0 – Off (default). use standard native resolving only (don’t use TRR at all)
1 – Reserved (used to be Race mode)
2 – First. Use TRR first, and only if the name resolve fails use the native resolver as a fallback.
3 – Only. Only use TRR, never use the native resolver.
Up to FF >= 73, this mode also requires the bootstrapAddress pref to be set.
Starting with Firefox 74, setting the bootstrap address is no longer mandatory – the browser will simply bootstrap itself using regular DNS, unless the DoH server domain can’t be resolved.
The native resolver will still be used for portal detection and telemetry (Bug 1593873)
4 – Reserved (used to be Shadow mode)
5 – Off by choice. This is the same as 0 but marks it as done by choice and not done by default.
I run my own DNS it wouldn’t make a lick of difference if they enabled that feature or not.
My question to the author is why do you rely on your isp or google for dns provision?
Just route all traffic going through your client pc to a raspberry pi server running both a local dns and vpn to handle internet exchange, make sure to use a strong firewall and only route open and in use ports on the pi. You will be your own dns and vpn provider essentially, nice way to get around all the bull plop security advisors be damned.
Also use encrypted connections with scrammbled keys and remember to drink your beer cold!
Cloudflare criticism and controversies courtesy of Wikipedia for what it’s worth: https://en.wikipedia.org/wiki/Cloudflare#Criticism_and_controversies
Yes, it is especially because Cloudfare cannot be trusted — and they still hate Tor users.
am i behind the times using DNS over TLS ! things change so fast…
https://tenta.com/
Is there a good technical (or otherwise compelling) reason why FF is bypassing the Hosts file.
I (maybe mistakingly) consider the Hosts file to be part of the operating system. Therefore it is none of FF business. FF should concentrate on making a BROWSER; that is already enough of a challenge from them.
It’s a “side-effect” (or more likely a deliberately built in feature) of the protocol. Firefox didn’t create the protocol, they are just adhering to the open standard.
https://en.wikipedia.org/wiki/DNS_over_HTTPS
“The goal of the method is to increase user privacy and security by preventing eavesdropping and manipulation of DNS data by man-in-the-middle attacks”
Don’t know about you, but I would call hosts a MitM attack (it intercepts and changes data)
Just as long as people are aware that patching one “hole” can open others. The internet was never designed from the ground up with privacy or security in mind, and all they have ever done since is apply bandaid after bandaid
“Don’t know about you, but I would call hosts a MitM attack (it intercepts and changes data)”
Considering in that case that the man in the middle controlling the Hosts is me, certainly not a MitM “attack”.
Obviously I am not calling your specific actions a MitM (eg if you manually add content to hosts), but the mechanism can be used for bad things too – can you always be sure it was you controlling it (maybe you were hacked? maybe some shitty software modified it?). The point is that the spec tries to eliminates these possible holes (I have not read the spec, so I’m kinda assuming here).
On the other hand I consider the Mozilla in The Middle like a real “attack”.
Also I found this very interesting, worrying!
https://forum.palemoon.org/viewtopic.php?f=4&t=19826&sid=d7d985813a5e4a4b2d4df40f45da30fe#p147067
Sob__: The trouble is, if DOH or similar technology becomes available everywhere by default, DNS-based filtering will stop working even for non-technical users. And guess what, censors won’t say “oh well, we tried, there’s no point to continue now, let them have uncensored internet”. No, they will move to other (worse) forms of filtering. For web browsing, it’s very easy to block access to selected hostnames. It’s much more resource intensive than DNS-based solution, but possible. A government that really likes censorship will happily pay for ISP’s costs with own money. Well, not exactly “own”, they will tax you to get it.
It’s a MitM attack considering it intervenes within a connection in order to modify it. The difference is of course that you’re the man behind the man and that the attack is aimed at defense. But semantically I have to agree with Pants as well as with “patching one “hole†can open others.” which is so true.
Not to mention that it is likely that “real” MitM attackers may be reasoning as we do with a Hosts file : it’s for one’s good! The problem is who’s?!
That’s the whole difference between theory and practice :=)
I’ve got my system set to run through Cloudflare’s DNS resolver, largely because I wasn’t left screaming “why?!” to myself when thumbing through the privacy policy. From the tests I’ve run, it’s by far the fastest resolver for me to run, so that’s definitely a plus.
Just a selling point– 1.1.1.1 is one of the few DNS resolvers that protects against DNS rebinding. Shrug.
I suggest to read
https://www.heise.de/newsticker/meldung/Trusted-Recursive-Resolver-Kritik-an-neuer-Sicherheitsfunktion-fuer-Firefox-4130296.html
That is quite more informative than what i read here, including the comments from the “experts”.
my perception: heise.de and most of its users are well-known misanthropic extremists/populists. appropriate and journalistically balanced to the topic: ghacks & golem (https://www.golem.de/news/dns-over-https-hoster-haelt-doh-im-firefox-fuer-gefaehrlich-1808-135854-2.html) . this also includes the corresponding user reactions. but everyone as he wants.
@ noemata
my perception: heise.de and most of its users are well-known misanthropic extremists/populists.
What have you been smoking or inhaling lately?
@jan: just such an “answer” fits perfectly to the corresponding attachment in this tweet: https://twitter.com/thigles/status/1025649452286193664 . ps: after all & and back to the topic: https://bugzilla.mozilla.org/show_bug.cgi?id=1475321 or https://translate.google.com/translate?hl=en&sl=de&tl=en&u=https%3A%2F%2Fwww.privacy-handbuch.de%2Fdiskussion.htm (05.08.2018) or https://download.dnscrypt.info/dnscrypt-resolvers/v2/public-resolvers.md and so on and so forth, i think martins conclusion is right: “it is too early to come to a conclusion”. a paradox. but i like that. pps: apologies to all english users in an english-speaking forum on an english-speaking site. heise.de, which i already know/read since 1999 ( https://web.archive.org/web/19990430011141/http://www.heise.de:80/ ) .. it’s such a typical german thing. i promise i won’t go into that again here on ghacks :) .
Sorry for typos, it was about time to change keyboard batteries
… wise decision, I’m glad I did.
The fun part of this discussion is, most of you don’t trust Cloudflare at all. But all of you express your concerns on a website hosted on CLOUDFLARENET – Cloudflare, Inc., US
gHacks.net WHOIS, DNS, & Domain Info — http://whois.domaintools.com/ghacks.net
I encourage all of the sceptics now to encrypt their comments in the future in such a enigmatic way, so the rest of us can’t read nor understand this prophets of doom anymore … or alternate read the docs.
@noemata
Quote: “[…] it’s such a typical german thing. i promise i won’t go into that again here on ghacks :)
… wise decission, but I’am glad you dit ;-)
Thanks for all of your references!
@Daniel
The simple point is
” … or alternate read the docs”
par example
https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+-+The+Problem
https://hacks.mozilla.org/2018/05/a-cartoon-intro-to-dns-over-https/#comment-23397
https://github.com/curl/curl/wiki/DNS-over-HTTPS#publicly-available-servers
[…] et al.
would have prevented much of this nonsensical flurry in this forum and elsewhere. Fefe_ism à la “Firefox continues to wage war against its user” is not about raising awareness, but creates the desired clickbait for these “security experts”.
I assume we can agree about this point.
@ mouche : The complaining may sound funny, but it’s not really the case though, is it?
In 2014 CloudFlare was estimated to deliver ~5% of all internet traffic, in 2016 it was said to be up to 10% and that number surely has only grown since, because the company also enjoyed talking about growth rates of 40 respectively 80% in 2017. Judging by information on their website, the company claims to route almost 40% of global DNS traffic right now.
With that kind of prevalence, you can’t “do” the Internet without CloudFlare anymore and even if you dislike or distrust the company, the only options are to abstain almost totally or accept it silently.
The only problems *I* have with CloudFlare are that half a somewhat using false-advertising and half the slow formation of a monopoly.
To the latter, we Europeans are more sensitive to that than the rest of the world and maybe too much of it at times, I grant you.
To the former, its DDOS protection and the other attached features require for CloudFlare to act as a Man-in-the-Middle. In other words, any secure connection you make to a server that is being protected by CloudFlare is, for a brief moment, unencrypted in the hands of a company under US jurisdiction and that often happens without your knowledge or consent. I say without either because in many cases the user sees no visible signs unless the CF customer activates higher security measures that are visible in the browser.
Misanthropy is certainly not the best skin for a populist :=)
@tom hawack .. that’s why populists are so dangerous and seductive. a strange world we live in :)
@noemata, I agree that populism is dangerous especially that it seduces narrow-minds and them only. Yet I cannot imagine a misanthrope being at the same time populist, doesn’t fit.
@tom hawack .. maybe you cannot imagine a misanthrope being at the same time populist, because populists are seductive. sry for o.t. .
@noemata, being seductive relates to one’s behavior rather than to his personality. A misanthrope can be seductive if he decides to and a populist quite antipathetic when/if he forgets his audience. I’m referring to what we are not to what we appear to be. In my view a misanthrope is lost in a deep sorrow regarding mankind, mankind therefor is unlikely to trigger whatever social approach in his mind and perhaps especially not populism which would be in total contradiction with his philosophy of mankind. On the other hand i’d consider a populist as forged with short-term long-haul binary and short-minded views of society : he is not misanthropic, disappointed but extroverted towards society and introverted towards brotherhood.
I may speak here for myself (what better example then ourselves as Montaigne noted it), being tempted by my mind to lean towards misanthropy and called back by my soul to consider individuals before society, which allows to keep hope. And I couldn’t imagine myself arguing of my occasional misanthropy to exercise populist conclusions.
@tom .. sorry, i cannot see any contradiction here. please don’t make me take a “famous” example (hitler & co., “group-based misanthropy”, right wing populist misanthropy against a spectrum of social groups and the deeper, resp. underlying, more basic and hidden “individual – misanthropy” in this context, et cetera. for me, populism is only a mask. only “the skin”, a secondary phenomenon. what i can “see” resp. what it appears to be. that’s all. but what is really going on? well, populists are seductive. that’s the point that undermines the apparent contradiction in the context of misanthropy. i understand your philosophical point of view. but my view on this topic is maybe a little bit different.
@noemata, “group-based misanthropyâ€, “right wing populist misanthropy” doesn’t mean anything as well as a considerable amount of what we read is arguable for the least. But, OK, I or course respect your commitment to whatever literature.
@noemata, you write “well, populists are seductive.”. I linger to discover the slightest seduction in a populist’s phantasms or even in the way they are proclaimed. Being seduced by the style, even within disgreament on the content, is itself dangerous. Take care.
Thanks for the info & link, jan.
I haven’t read anyone here proclaiming himself an expert, we’re only debating free of pretentiousness (as I felt it).
“Mozilla’s new DNS resolution is dangerous” is just clickbait for the uninformed and the tin foil hat wearing conspiracy theorists. I mean no disrespect to the people who believe in Sasquatch or to those that are scared to walk their dog at night for fear of the Boogeyman. LoL. Sorry, I had to say it. :)
“The feature is only available in Firefox Nightly at the time of writing”
I don’t know about everyone else but it’s been working for me in Firefox stable since v61 was released and I used it (TRR only) for a couple weeks. I just updated FF stable to 62 Beta 14 a couple days ago and it’s working with that also. And, I’ve been using it in Nightly for a couple months. Still using it in Nightly without ever participating in the Shield study.
“Single point of failure: if Cloudflare goes down, down goes the ability to browse the Internet.”
That depends on the “network.trr.mode” that is being used.
Mode #1 will use TRR or the native system resolver depending on which one is faster.
Mode #2 will use TRR and then fall back to the system if TRR fails.
Mode #3 will Only use TRR, if it fails… “Hmm. We’re having trouble finding that site.” :)
“That’s why we have alternative DNS server address” Which will be completely ignored if using mode 3.
In my experience when using mode 1 or 2 it will almost always use the native resolver which can be seen when opening the page about:networking#dns in FF, which is why I’ve been using mode 3 (TRR only) the vast majority of the time. Don’t have a clue why modes 1 or 2 will so often fail to use TRR. I left TRR mode 3 enabled all this time in Nightly because I’ve never seen an increase in page load times or Any failed network requests, otherwise I would have stopped using it. In FF I’m also using a longer than default network dns cache expiration which I think would make failed requests more noticeable. And using “TRR only” in Nightly is fine for me because it’s not my primary browser and I have other browsers that I can use.
As Pants mentioned and I can verify, a hosts file will Not be used when using TRR in FF. I personally don’t like that but… in browser content blocking will always have faster page load times than a hosts file and in browser content blocking will be much more precise with what it blocks. But still, I like having my hosts file as a backup. Another thought is how many using a hosts file only rely on that hosts file and don’t use any in browser content blocking? I would be shocked if anyone that went through the effort of setting up a hosts file wasn’t also using multiple methods of content blocking and going without any element hiding. The Horror!
The odds of Mozilla actually enabling TRR as an opt-out feature are slim to none. JMO. Too many laws would be broken. I would like to see Mozilla implement a 1st party service but I would be very surprised if that ever happened. Anyway, I don’t use the DNS service provided by my ISP so I can wait to see how it works out before using it full-time in FF stable. If I ever do use it, in FF stable. As Tom mentioned, I’m also more concerned about Who is providing my DNS service rather than if it’s being encrypted.
My about:config settings for Nightly that also works in stable:
user_pref(“network.trr.bootstrapAddress”, “104.16.112.25”);
user_pref(“network.trr.mode”, 3);
user_pref(“network.trr.uri”, “https://mozilla.cloudflare-dns.com/dns-query”);
Preferences:
“https://gist.github.com/bagder/5e29101079e9ac78920ba2fc718aceec”
1) “Mozilla’s new DNS resolution is dangerous†is just clickbait for the uninformed and the tin foil hat wearing conspiracy theorists. I mean no disrespect to the people who believe in Sasquatch or to those that are scared to walk their dog at night for fear of the Boogeyman. LoL. Sorry, I had to say it. :)
> “conspiracy theorists”: So for you someone not trusting Cloudflare or Mozilla is a conspiracy theorist.. no comment.
2) “I would be shocked if anyone that went through the effort of setting up a hosts file wasn’t also using multiple methods of content blocking and going without any element hiding. The Horror!” From Pants: “I just hope people realize that using DoH (as an application layer DNS) bypasses for example on windows, your hosts file.”
> In summary two approaches, yours aggressive in some points while Pants is respectful, just saying. Hosts file is more secure while for example with only Ublock Origin filters can be ineffective until you refresh the page, it depends on the ad-blocker used. So yes bypassing the Hosts file can be dangerous, whether you like it or not.
“So for you someone not trusting Cloudflare or Mozilla is a conspiracy theorist..”
You took two words out of a fairly long sentence and used them out of context to try and make a point/accusation. Why is that so typical nowadays???
Theorists, conspiracy theorists, and “tin foil hat wearing conspiracy theorists” are three entirely different things in my eyes. Am I the only one that can see that? That’s funny and sad!
“tin foil hat” as expression looks like a borborygme that should be only used by Trump on Twitter, that’s why I did not pointed it.
“should be only used by Trump on Twitter” That sounds very much like you want to censor my speech. You go girl! LoL
Maybe we can agree to disagree. If not so be it.
Bypassing the hosts file in my opinion is more annoying than dangerous. Maybe disconcerting would be a good adjective to use. If… you are Only using a hosts file then obviously you don’t want to use TRR. Are you saying you only use a hosts file? I’m using uBO, No-Script and FF Tracking Protection so I have three layers of content blocking before my hosts file even comes into play. Basically, it’s just taking up space on my hard drive and I’m okay with it continuing to just take up space. Dangerous? Not feeling it when I use Nightly with TRR, sorry.
I’ve personally never experienced uBO needing a page refresh for it to work. I spend a lot of time using a hosts file that only uses malware and cryptojacking entries and I would notice if content wasn’t being blocked or if elements weren’t being hidden, or if my 97 personal Filters weren’t being used, or if my 173 personal Rules weren’t being used, I would notice. I started using uBO back when it was only available on github and even before uBO I honestly don’t remember having to refresh a page for ABP to work. Is that supposed to be a thing now? Is anyone else seeing filters not working in uBO? If that’s what you’re seeing something’s wrong. I can only say that I’m not seeing any problems like that on my hardware, with any of my 3 FF profiles or for that matter in any of my 7 browser installs. Am I just lucky? Did I win the jackpot? That’ll never happen. :)
I do know Chrome has a problem loading working extensions at startup but after startup all is well. Rarely does FF have a problem loading working extensions at startup. I have all of my browsers configured in such a way that I can see if 3 different extensions are working at startup, or not.
If you feel that bypassing the hosts file is dangerous then that is your prerogative. If you don’t want to trust Cloudflare or Mozilla fine, configure your browser accordingly. If your mission was to convince me of the error of my ways then you’ve failed. I do appreciate the effort though. Just saying… Danger Will Robinson!!! :)
Peace!
“I started using uBO back when it was only available on github and even before uBO I honestly don’t remember having to refresh a page for ABP to work”
It can’t happen with ABP, it’s by design. Ask to gorhill (if he wants to answer).
I have some fairly serious security concerns over this effort, personally, but nobody listens to me, so all I can do is make sure that I personally never use this.
If it were opt in, lack of expertise would cause Aunt Millie, Grandpa, and little Johnny to never use this FF feature as a ‘privacy enhancer’. I think Mozilla is trying to do right for their users and I think this is a good thing overall. I like Cloudflare for many reasons. They offer excellent services and often take actions that are not in their best interest. …and since Cisco bought OpenDNS, which was a less than lovely event, I’ve used other services such as Cloudflare; especially after their April fools ‘4 ONE event’.
DNSCrypt is excellent for many reasons but unless your run your own dns server, it does little to protect your privacy when it comes to lookups. If you are in the corrupted US, your extremely greedy ISP can illegally spy on every single site you visit: for their profit and your privacy loss. Sites that are seemingly private, such as multi hosted domains similar to tumblr, leak the exact site name of your encrypted visit giving away what you are interested in. For these multi hosted domains, the fly in the ointment is a field named Server Name Indication (SNI). Until researchers develop a method to mask the clear text data sent in the SNI field, your ISP can mine every ‘hidden’ subdomain you visit; just as though they were “serving” your dns request. This statement assumes they have competent spies, errr I mean programmers, writing their illegal wiretaps against their *paying* customers. (I say illegal because 20 years ago, ISPs would have gone to prison for these illegal wiretaps. These days, corrupt US law is written by corrupt/greedy multinational corporations and given to the bribed, corrupt monkeys in the US congress who pass it for tainted peanuts. I think I’ve become a bit cynical the past 40 years thanks to neoliberalism absolutely destroying my country).
OK, that said, I still use Cloudflare. It’s a long shot that my ISP might not be paying their programmers enough to be creative; enough to do the extra work to capture the SNI field let alone the dns request. I suspect for now, ISPs are going after low hanging fruit and just mining the sites visited and possibly the dns request. If interested in dns request and if this FF feature catches on, it will only be a matter of time before ISPs get more creative.
The irony in all of this? Ad blockers are slowly becoming main stream. All of this spying for ad revenue will eventually dry up and hopefully bring us back to the good old days on the inet; the era before unfettered greed ruined it.
Thank you so much for the great article and comments, what a great community !
I remember an interview of famous Apollo 1 commander, Neil Armstrong, stating “I smoke one cigar a month but sometimes i forget to”. Same here : we smile but sometimes we forget to (and the fact that everything works out better with a smile) :=)
Apollo 11, of course. Sorry, Neil!
There’s another, less-highlighted, issue here: If “d’Oh!” (as I call it) is opt-out, then there’s a potential legal problem: In some regions, areas and organizations you are required by law to use supplied DNS servers (using anything else is seen as circumventing established regulations). Even something as simple as deploying Firefox in e.g. a school with basic safe browsing guards or DNS-based parental controls and safebrowsing becomes moot as it’s bypassed this way.
I guess Mozilla wants to lose more of its user base by making it risky to have users use it, bypassing safeguards and regulations?
@moonchild wrote “I guess Mozilla wants to lose more of its user base by making it risky to have users use it, bypassing safeguards and regulations?”
This remains conditional but indeed, if adopted as opt-out (and even opt-in IMO) would deserve your remark.
At the European parliament Mozilla is regularly making lobbying to change our laws like about copyright etc. Now Mozilla wants to redirect european people to servers making them dependent on US laws, WTF?
@ anonymous: “At the European parliament Mozilla is regularly making lobbying to change our laws like about copyright etc. Now Mozilla wants to redirect european people to servers making them dependent on US laws, WTF?”
https://securedns.eu/ . try it. slow experience. cloudflare has the better infrastructure all over the world for a fast dns-hosting-service. should mozilla build their own dns-hosting-service? impossible for mozilla. to expensive. too complex. impossible. so should DoH be abandoned in general and for all the future, because nothing and nobody can be trusted? not really. as always it is necessary to find a middle way. “@mozilla” : this also implies, of course, to give the user the choice which dns service he uses for DoH.
@noemata: Not a question to be trusted or not trusted here. The question is e.g Cloudflare with which Mozilla apparently is now in business is subject to the US laws. Microsoft with Windows 10 to avoid prosecution was already warned by the European Commission to transfer its servers in Europe. If Mozilla wants to lose confidence of european people well they just have to continue in that way.
@Anonymous ..yes, i agree on that point. maybe, there is something interesting going on .. here: https://bugzilla.mozilla.org/show_bug.cgi?id=1475321#c2 .
@noemata,
“so should DoH be abandoned in general and for all the future, because nothing and nobody can be trusted?”
It should be abandoned, not because “nothing and nobody can be trusted” but because some things and some people should definitely be. IMO DoH could very well be an attempt to gather DNS requests (with the ultimate tracking features it implies) on the basis of a trending users’ quest for privacy. Of course not being a specialist means use of conditional in my words and in my thoughts but as far as i’m concerned the DNS resolver is far more important than the request being encrypted or not.
@Tom Hawack .. maybe you are right about this point resp. alternative point of view. i’m going to read your contributions more accurately, lets see if i understand them.
@noemata, you’d certainly understand better if I write correctly, i.e. above,
“It should be abandoned, not because “nothing and nobody can be trusted†but because some things and some people should definitely not be”
Inversions, like some leaders at a press conference :=)
1.) everything is said, especially from user “anonymous” : “It’s just a matter to who you want to give your data. Your ISP? OpenDNS? Google? Cloudflare? It’s your choice” . 2.) the advantages outweigh the disadvantages 3.) if you use DoH (quote from: https://www.privacy-handbuch.de/handbuch_21w.htm) : .. “If you want to use TRR-Mode 1-3, you have to disable the validation of SSL certificates via OCSP server. Otherwise the cat bites its tail. Firefox wants to check the SSL certificate of the DNS-over-HTTPS server and needs the IP address of the OCSP server from the DNS-over-HTTPS server. Solution to the problem: security.OCSP.enabled = 0 ” . 4) the 1.1.1.1. policy: https://developers.cloudflare.com/1.1.1.1/commitment-to-privacy/privacy-policy/privacy-policy/ . 5) should they use googles DoH server, really? read their policy 6) alternative to 1.1.1.1. with no-logging-policy: https://securedns.eu/ ; slow in comparison to cloudflare 7) do not use mozillas cloudflare DoH server. use the official cloudflare DoH server: network.trr.uri = https://cloudflare-dns.com/dns-query .
ps: sry to point 7.) : https://bugzilla.mozilla.org/show_bug.cgi?id=1475321#c2 . mozillas shield – study is over. therefore, mozillas cloudflare DoH server is now usable (you just have to have the choice) . stricter policy: https://developers.cloudflare.com/1.1.1.1/commitment-to-privacy/privacy-policy/firefox/ .
I wish and intend to be the only one who chooses my DNS resolver. Mozilla’s new DNS feature, should it be opt-out (unlikely according to the article) would be determinant for me to avoid it and denigrate it.
I dislike the idea of having a specific DNS resolver for a given application.
I wish to be able to change on the fly my system-wide DNS resolvers (as this is the case).
I don’t have a systematic confidence in companies’ promises:
“Mozilla signed a deal with Cloudflare for the test. Cloudflare agreed to even stronger privacy terms.”
May we read that deal, is it signed, in what terms, to what extent does it oblige both parties? Companies lye and remain bound to legal matters and even then: on the tangent.
Personally, I’ve switched from DNSCrypt-proxy to ‘Acrylic DNS Proxy’ because I didn’t find in the former an encrypted DNS resolver located in my country that would meet fast resolving (only one, slow and unreliable IMO), because the latter allows me to choose whatever DNS resolver and performs excellently well in terms of speed (with enhanced caching feature) together with an enhanced HOSTS blocking infrastructure. I generally set Acrylic to use FDN (French Data Network) servers, reliable and fast. No longer encrypted DNS requests with Acrylic (though Acrylic can be set to work with DNSCrypt-proxy) and so what, not that important to me.
My general policy concerning the OS, Web apps, services is to connect as far as possible within Europe, cloud hosting as well and maybe before all. I am extremely suspicious about my data transiting via (remaining moreover) U.S. based servers for the sole reason that the U.S.A. is becoming the business’ ally rather than the users’, not to mention US intelligence privacy intrusions : the Web freedom’s and privacy Eldorado is in Europe now.
> Single point of failure: if Cloudflare goes down, down goes the ability to browse the Internet.
For the study, the addresses fetched by the OS are the ones used, so if Cloudflare goes down it wouldn’t affect those in the study.
For those who decide to use DNS Over HTTPS, one of the options (network.trr.mode=2) is to use DOH first and, if that fails, fetch the address from the OS. Another option (network.trr.mode=1) is to send requests by both Native (OS) and DoH and use whichever returns first. Either of those options would eliminate the DoH as the single point of failure unless, of course, both the OS and DoH are using exclusively the same DNS server.
That’s nothing new. The same discussion has been led four months ago on the Firefox subreddit r/Firefox ( https://www.reddit.com/r/firefox/comments/85nlj3/cave_mozilla_is_about_to_launch_a_shield_study/ ) and people weren’t enthusiastic about it back then either, although from what I remember the most critical voices, in the early days when this study was still being discussed internally at Firefox, were focused on a) informing users properly and b) user consent prior to activation.
Personally Cloudflare is far from my favorite web service, but today you won’t get a functional Internet if you’re not willing to use their services so you’re stuck anyway. They already offer a free and privacy-minded DNS server – remember it’s the 1.1.1.1 IP address – and if their DoH server that is being used in the Firefox study uses the same privacy policy, then I don’t think things are as bad as they’re made out to be by the harshest critics.
That said, one of the biggest problems *I* have with the whole thing is that the web-browser cannot know how a user configured the DNS on his computer or in the local network. There’s no difference to the browser whether I use the default DNS server of my ISP, a Google DNS or whether I chose to run a local DNScrypt proxy on my PC or anywhere else in the network for that matter. Then there are people who use DNS for other purposes such as to block ads via Pi-hole to name just one example.
Switching how the browser requests a domain name lookup without the user’s explicit consent (or even knowledge, as it was initially being planned) can not only have privacy implications but may also change functionality in ways that are not desired. Considering these points, I don’t get why the people preparing this study were against informing users they had been switched to DoH.
They’re being informed about their participation now I hope? I have to admit that I didn’t really follow the developments further, the only thing I did was to check my Firefox profiles had disabled any kind of studies so this couldn’t be sneaked in.
Full disclosure, I’m running a local DNS server in the form of Pi-hole which connects to upstream servers via the DNSCrypt protocol.
IMO, for most users, it is better to control DNS from an OS or network layer. There are definitely uses for DoH thought – and it attempts to solve some problems, of which there are many in DNS.
I just hope people realize that using DoH (as an application layer DNS) bypasses for example on windows, your hosts file. And that all you are generally doing is giving away your DNS queries to a third party (your ISP would already be able to log domains you visit anyway). If you’re using a VPN, then use that VPN’s DNS service.
In other words, stop duplicating the data between parties if you can.
PS: I am not an expert on DNS, DNSSEC, DNSCrypt etc, and I’ll defer to Daniel above :)
Full disclosure: I use OpenDNS’s servers (set at router and os level) and run OpenDNSCrypt (Windows)
There are advantanges and disadvantages of DNS over HTTPS. In controlled envrionment this is a good feature. It can bypass certain block by organization or ISP, usually changing dns in your computer or router won’t work because they already poison the dns query(dns poisoning) on the higher level
“bypasses for example on windows, your hosts file” Thanks for this essential info.
> In my case using HostsMan, “is Mozilla’s new DNS feature really dangerous?” > YES.
@Pants, “I just hope people realize that using DoH (as an application layer DNS) bypasses for example on windows, your hosts file.”
I wasn’t aware of this. Good to know.
>Single point of failure: if Cloudflare goes down, down goes the ability to browse the Internet.
That’s why we have alternative DNS server address
>Cloudflare is a U.S. company and a third-party.
It’s just a matter to who you want to give your data. Your ISP? OpenDNS? Google? Cloudflare? It’s your choice
What’s the potential advantage to the end user of Mozilla using Cloudfire for DNS lookups instead of the ones your ISP provides? Sometimes folks get caught up in pointing out the potential issues with something, and I never even get to hear the reason the folks who may be or are making the change give for it.
Would Mozilla say that Cloudfire could be faster at DNS lookups than your ISP? What would they tell me to persuade me that this was a good potential change?
Does using a third-party DNS resolver mean that your ISP no longer has a record, and it goes to the third-party provider instead, or do you just now have two parties with records instead of one?
Cloudflare have made it abundantly clear that they don’t wanna know what their dns users are doing via their service. They don’t log any data, so to say that they would benefit by getting dns queries from Firefox users sounds absurd.
It’s a myth that Cloudflare doesn’t log the data… https://blog.apnic.net/2018/04/02/apnic-labs-enters-into-a-research-agreement-with-cloudflare/
All we have for that is Cloudflare’s word. Seems like weak sauce to me.
A US company lying. Shocking.
I’m just curious. How does CloudFlare make its service profitable?
CloudFlare watches traffic so it has great potential for analysis and selling world traffic statistics (not tied personally to specific users) so called ‘Internet monitoring’ I suppose. It may be profitable on a large scale.
Firefox Nightly will update(s) 2 times per day.
What is with intranet sites which are only known by local dns servers?
Unknown at this point. Controls will become available through policies.
I am already using the DoH feature in Firefox but with a provider i trust. Not Cloudflare. As long as i can choose the DNS provider, i don’t see any problem.
Which DNS provider did you choose?