Workaround for the Windows Print Spooler Remote Code Execution Vulnerability
Microsoft disclosed a new remote code execution vulnerability in Windows recently that is using the Windows Print Spooler. The vulnerability is actively exploited and Microsoft published two workarounds to protect systems from being attacked.
The provided information is insufficient, as Microsoft does not even disclose the versions of Windows that are affected by the security issue. From the looks of it, it seems to affect domain controllers for the most part and not the majority of home computers, as it requires remote authenticated users.
Update: Microsoft released out of band updates to address the printing related vulnerability. You find links to the patches on this Microsoft page. End
0Patch, who have analyzed the patch, suggest that the issue affects Windows Server versions predominantly, but that Windows 10 systems and non-DC servers may also be affected if changes have been made to the default configuration:
UAC (User Account Control) is completely disabled
PointAndPrint NoWarningNoElevationOnInstall is enabled
The CVE offers the following description:
A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
An attack must involve an authenticated user calling RpcAddPrinterDriverEx().
Please ensure that you have applied the security updates released on June 8, 2021, and see the FAQ and Workaround sections in this CVE for information on how to help protect your system from this vulnerability.
Microsoft provides two suggestions: to disable the Print Spooler service or to disable inbound remote printing using the Group Policy. The first workaround disables printing, local and remote, on the device. It may be a solution on systems on which print functionality is not required, but it is not really an option if printing is done on a device. You may toggle the Print Spooler on demand, but that can become a nuisance quickly.
The second workaround requires access to the Group Policy, which is only available on Pro and Enterprise versions of Windows.
Here are both workarounds:

To disable the print spooler, do the following:
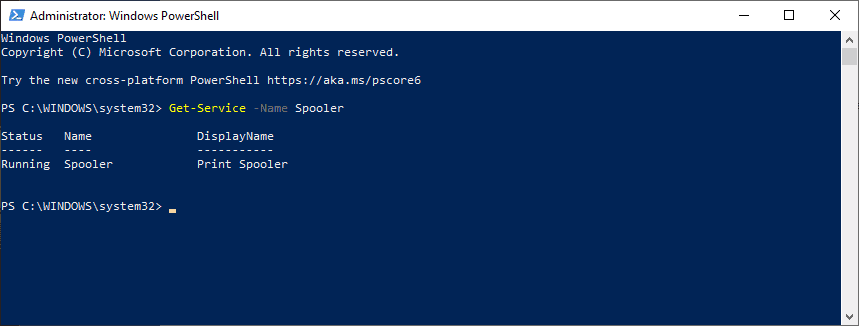
- Open an elevated PowerShell prompt, e.g. by using Windows-X and selecting Windows PowerShell (Admin).
- Run Get-Service -Name Spooler.
- Run Stop-Service -Name Spooler -Force
- Stop-Service -Name Spooler -Force
- Set-Service -Name Spooler -StartupType Disabled
Command (4) stops the Print Spooler service, command (5) disables it. Note that you won't be able to print anymore when you make the changes (unless you enable the Print Spooler service again.
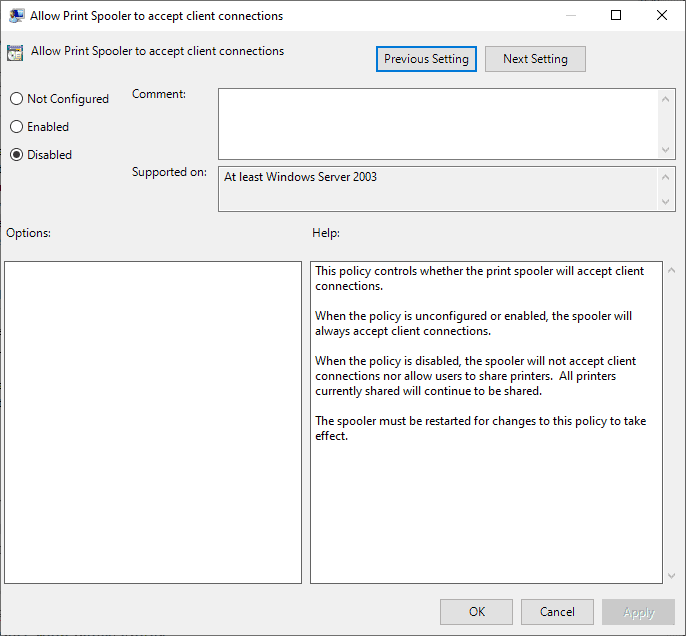
To disable inbound remote printing, do the following:
- Open Start.
- Type gpedit.msc.
- Load the Group Policy Editor.
- Go to Computer Configuration / Administrative Templates / Printers.
- Double-click on Allow Print Spooler to accept client connections.
- Set the policy to Disabled.
- Select ok.
0Patch has developed and published a micropatch that fixes the Print Spooler Remote Code Execution issue. The patch has been created for Windows Server only at the time, specifically Windows Server 2008 R2, Windows Server 2021, Windows Server 2016 and Windows Server 2019.



















I already had this feature turned off and disable, as I don’t have a printer, and I thought it was a security risk.
How about Microsoft invents “an on/off button” for the print spooler, and puts it
right on the Desktop.
For example, I recommend that they look at the concept of the
“light switch”. Most light switches entail a specific “on position”
and an “off position”, right there on the same switch.
This is different from some Microsoft switches, which either can easily be
turned on, but turning them off requires going into the basement and finding
the off switch under the furnace. MSFT also has off switches that can be turned off without much ado, but turning them ON again requires 25 times
the ado. Of course, some version of Windows have switches that can neither be turned off or on. So, in general, Microsoft has the “let’s make this as complicated as possible” method pretty well covered.
I have no idea where their complete lack of common sense comes from.
Why stop with print spooler? They should put all on/off buttons for everything on the desktop. Sure your desktop would have thousands of buttons on it, but at least they would be in place where idiots like me could find it eventually, instead of having them organized out of site for power users who know what they are doing.
Where do we disable the function that makes new ink cartridges cost more than a new printer?
Alwyas buy Brother laser printers. Stop buying crappy HP, Epson and Canon, inkjet printers.
RE: Where do we disable the function that makes new ink cartridges cost more than a new printer?
Snarky response: Been there, bought new printer just for the cartridge. Printer manufacturers got wise to that idea, and now new printers have cartridges that are only about 20% or 30% full, so you have to buy a new printer even more often.
Helpful response: If printing in black and white is your thing, there are several Brother Laser printers that have toner cartridges lasting between 5,000 to 8,000 pages. Brother has the cheapest way to print in black and white. I never use ink jets, which have cornered the market on the most expensive way to print.
According to MS’ Security Alert https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527 you don”t have to disable the print spooler to avoid trouble – only the ‘inbound remote printing’ function:
Option 2 – Disable inbound remote printing through Group Policy
You can also configure the settings via Group Policy as follows:
Computer Configuration / Administrative Templates / Printers
Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
Impact of workaround This policy will block the remote attack vector by preventing inbound remote printing operations. The system will no longer function as a print server, but local printing to a directly attached device will still be possible.
Is mandatory workaround for all printer vendor or some are excluded?
I guess this means for a typical user at home, with a central printer other computers on the home network can access, there are no issues. If printer access through the internet is allowed, there’s an issue?
Kinda confusing, the Win Server issues are clear but all machines networked or not have a print spooler to queue print jobs ‘cuz printers take a while to print.
I hate installing printer drivers, they’re almost a virus. Between the new printer showing up multiple times in weird places and the begware GUI’s manufacturers use, getting a print at all is a relief. If your printer will allow it, Windows will print just fine with its own drivers.
Able Youth Foundation said on July 3, 2021 at 8:26 am
Hi,Whilst in services, don`t forget to disable recovery option to “NO”.Thanks.Mike.
Or just block incoming connections to spoolsv.exe on firewall
LOL… MS doesn’t even disclose which versions of Windows this serious issue affects? Are they really that inept?
@inept?
Yes they do. Read this, it’s written in black and white:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527
The vulnerability is in all versions of Windows.
Those of us with vision disabilities and/or difficulties with typing can use this simpler, more efficient method for disabling the “Print Spooler” service…
Follow these steps:
1. Right-click on an empty space within your Windows Taskbar, and select “Start Task Manager” with your Left-click.
2. Navigate to the “Services” tab inside the Task Manager window, and then Left-click on the “Services…” button located in the lower right section of this window.
3. Locate the “Print Spooler” within the list in the “Services” window, and enter its properties by double clicking on it.
4. Under the “Service Status” click the “Stop” button, and under the “Startup Type” select “Disabled”
5. Click on Apply / Ok… to close the window and save the changes… and you are done.
Thanks for the article Softonic.
To Able Youth Foundation: Does this workaround with “Task-manager” & “Services” work on Windows 10 Home type computers?
NB:Able Youth Foundation said on July 3, 2021 at 8:26 am…
Hi,Whilst in services, don`t forget to disable recovery option to “NO”.Thanks.Mike