Pale Moon 25.6 ships with anti-fingerprinting option
We talked about a fingerprinting technique using Canvas before and explained how companies make use of the feature supported by all modern web browsers to track users across the Internet.
We also told you how to block Canvas fingerprinting in Firefox and Chrome.
The most recent update of Pale Moon, a Firefox spin-off, introduces a native option in the browser that should make it a lot harder for others to use Canvas to fingerprint the browser.
Tip: If you want to check if a fingerprint may be created of your browser to track you online, check out this online test.
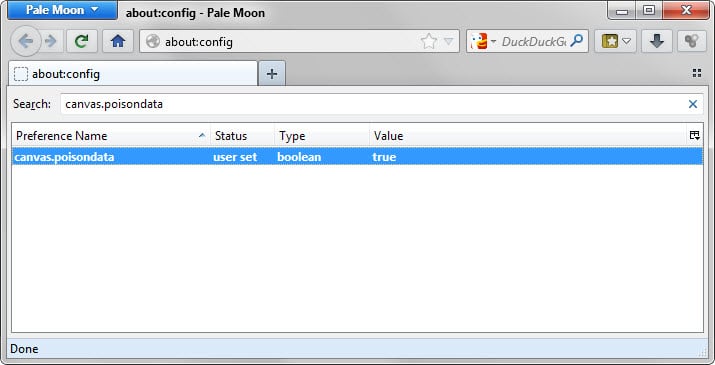
The new Poison Data option is not enabled by default in Pale Moon due to its impact on performance when Canvas is being used in the browser.
Pale Moon users can enable it in the following way:
- Type about:config in the browser's address bar and hit enter.
- Search for canvas.poisondata
- A double-click on the preference toggles its state.
To undo the change at any point in time, repeat the process described above.
So how do you know it is working? Simple, you visit the test page linked above and reload it a couple of times. You should get a new signature with every reload after you enable the Poison Data option in Pale Moon while the signature should not change at all without the preference (provided you don't use other defensive measures to protect your browser).
Anti-fingerprinting is definitely the core new feature of Pale Moon 25.6.0 but it is not the only one. Firefox users may recognize some of the features as Mozilla implemented them in Firefox in the past.
Here is a short rundown of the most important feature additions and changes in Pale Moon 25.6.0:
- Icon fonts are now loaded by default even if font loading is disabled. The feature will land in Firefox 41. The preference gfx.downloadable_fonts.enabled defines whether Firefox will download icon fonts automatically or not.
- The parameter autocomplete="off" is ignored by Pale Moon so that authentication information can be saved regardless of website preference. Users who want to disable the feature need to set signon.ignoreAutocomplete to false. A similar feature landed in Firefox 29.
- Screensavers are blocked automatically by Pale Moon if HTML5 video is played in fullscreen mode.
- CSP "nonce" keywords are now supported.
- Chrome://../skin/ overrides are supported now allowing users to customize browser icons.
- Several security fixes.
Details are provided by the official release notes. Existing users may use the browser's automatic update feature to update to Pale Moon 25.6.0 while new users find downloads for their operating system at the official project website.





















these are applicable to PaleMoon if anyone is interested:
//prevent mistyped urls in the location bar getting sent to google/yahoo etc
user_pref(“keyword.enabled”, false);
//prevent url mouseover opening connection to site
user_pref(“network.http.speculative-parallel-limit”, 0);
//disable search suggestions (prevent search box data being sent as you type)
user_pref(“browser.search.suggest.enabled”, false);
//prevent details being saved on secure sites
user_pref(“browser.formfill.saveHttpsForms”, false);
//don’t cache ssl sites
user_pref(“browser.cache.disk_cache_ssl”,false);
//don’t allow websites to alter browser history
user_pref(“browser.history.allowPopState”, false);
user_pref(“browser.history.allowPushState”, false);
user_pref(“browser.history.allowReplaceState”, false);
//don’t give web applications/google access to geo location, sensors or device battery status
user_pref(“geo.enabled”, false);
user_pref(“device.sensors.enabled”, false);
user_pref(“dom.battery.enabled;false”, false);
//don’t allow websites to mess about with right click menu, title/tool/menu/scroll bars
user_pref(“dom.event.contextmenu.enabled”, false);
user_pref(“dom.disable_window_open_feature.titlebar”, false);
user_pref(“dom.disable_window_open_feature.toolbar”, false);
user_pref(“dom.disable_window_open_feature.menubar”, false);
user_pref(“dom.disable_window_open_feature.scrollbars”, false);
user_pref(“dom.disable_window_open_feature.personalbar”, false);
//??
user_pref(“social.remote-install.enabled”, false);
//stop websites seeing and reacting to cut,copy and paste actions (but access to the clipboard via JS+Flash is not prevented)
user_pref(“dom.event.clipboardevents.enabled”,false);
Your settings for the 5 dom.disable_window_open_feature.xxx should be set to true, not to false (default is disable). This mistake happens when we have in mind that we wish to disable a feature and presume the setting is tied to enabled … the enemies of my enemies are my friends!
My apologies & gj with the swift correction.
user_pref(“dom.disable_window_open_feature.titlebar”, true);
user_pref(“dom.disable_window_open_feature.toolbar”, true);
user_pref(“dom.disable_window_open_feature.menubar”, true);
user_pref(“dom.disable_window_open_feature.scrollbars”, true);
user_pref(“dom.disable_window_open_feature.personalbar”, true);
..must have got lost in the copy paste frenzy. All this about:config fiddling is a bit unwieldy.
As I recall from the 2010 panopticlick project , using a minor browser/browser configuration and allowing JS was enough to uniquely identify you through various means. Also, optional measures to reduce fingerprintinting might even backfire, in a sense that they are only employed by a minority of users. It’s about getting all the privacy conscious users on a same indistinguishable wagon.
Poisoning/fake readout API:anti-Canvas fingerprinting techniques don’t point out the user as they are invisible to the Canvas hijacking performed by the site, contrarily to Canvas blocking (nonsense by the way since it may stop a site from running correctly).
As for Panopticlick the idea is a statistical likeliness to be recognized as part of a group determined by a number of parameters : the user is not recognized as such. But indeed one can wonder of the utility of anti-trackers when his IP is not hidden via a Proxy or VPN (when it is, panopticlick’s scheme is even more pertinent since it would mean that a Proxy/VPN user is doubly disadvantaged : 1- statistically “recognized” (spotted) and 2- if correctly tracked in time, the correlation between the user and his false IP established (imagine the user spotted with different IPs …).
Nevertheless, with or without a hidden true IP, breaking as many trackers as possible is always a good thing as it makes it harder to spot the user (how many are we on the Web?!) and that more users there are making life tougher for trackers is always good.
Now, 1- Most users don’t give a damn to be tracked, spotted and 2- for those who care, who have the consciousness of their dignity baffled when their privacy is (doesn’t mean others have no dignity, simply that they don’t understand it the same way), then for those of us who fight tracking as the pest we conceive it to be, let’s not forget that if we are not a target for one reason or another we are not likely to become the phobia of a whatever tracker ; at this time we are mainly statistics. But that’s already too much once you are aware that personal data even if not used never disappears and that if required one day by an intruder, can become a nightmare.
So, live and surf quietly or search for the devils and take a chance : if so, good luck.
Core feature is very nice
Actually this is only browser (besides TBB, but they just block, not poison)
who protect from canvas fingerprinting.
All other extensions are broken and vulnerable to bypass
(including Chameleon and CanvasBlocker, https://github.com/kkapsner/CanvasBlocker/issues/31)
Thanks for this valuable information.
I read on the Github’s page you mention that the CanvasBlocker bug is in a way only a “half-issue” considering that if a site uses the workaround (bypassing CanvasBlocker by using an iframe) then Firefox crashes … so it’s unlikely this method be used in the wild. But as the author of the issue puts it, “But i hope you fix CanvasBlocker before they fix FF :)“
“Tip: Ff you want to check if a fingerprint may be created of your browser to track you online, check out this online test.”
Should be
“Tip: If you want to check if a fingerprint may be created of your browser to track you online, check out this online test.”
Minor correct, another great article tho!
Thanks, corrected ;)
Great you mentioned it, I’ve been wondering until now what in the world Ff could mean!
Anti Canvas fingerprinting is provided as well on Firefox/Cyberfox browsers with the CanvasBlocker add-on (Firefox 26 and later) which includes the so-called poisoning feature named here the fake readout API :
“fake readout API: Canvas Blocker’s default setting, and my favorite! All websites not on the white list or black list can use the API to display something on the page, but the readout API is forced to return a new random value each time it is called.”
Poisoning/Fake is the only valid solution in anti Canvas fingerprinting, IMO, because otherwise some sites just won’t run (I remember New Google Maps which wouldn’t run with older version of CanvasBlocker which didn’t include the fake API option).
So, be it Firefox with CanvasBlocker or Pale Moon with the integrated Canvas poisoning feature (Bravo Pale Moon! -> Firefox : take example on Pale Moon!), both handle another of the Web’s hidden hijackings, when Canvas in itself is not more the problem than cookies are, but becomes problematic once hijacked. And both are, more and more, quasi systematically.
It should also be mentioned, that since version 25.6.0 Pale Moon for Linux is no longer available through SourceForge and people should go to http://linux.palemoon.org/ instead, also the installer script should be updated to the most recent version (which is at the moment 0.2.0).
Martin, did you bumped on Privacy Settings extension for Firefox yet?
Firefox’s Privacy Settings add-on doesn’t include anti-Canvas fingerprinting …
What do you mean by bumbed?
Found or saw a review by accident somewhere ;)
Anyway, it’s a really cool extension and I’m pretty sure that soon or later author will add switcher for preference you mentioned in post.